Unlocking Global Control: Real-World Remote IoT Access Examples
The Power of Remote IoT Access: Why It Matters
The Internet of Things (IoT) has fundamentally reshaped our interaction with the physical world, blurring the lines between the digital and the tangible. At the heart of this transformation lies the capability for remote IoT access. This isn't just about turning lights on and off from your phone; it's about unlocking profound efficiencies, enhancing safety, and creating entirely new service models. The ability to control and monitor your devices from anywhere empowers you to manage your environment, optimize energy usage, and stay connected to the things that matter most to you. These are just a few examples of the benefits of remote access to IoT devices.Personal Convenience and Unprecedented Control
For the individual consumer, remote IoT access brings a level of convenience previously unimaginable. Imagine controlling your smart coffee maker from thousands of miles away, ensuring your morning brew is ready precisely when you arrive home. This seemingly simple act is a powerful illustration of the control offered by remote access to IoT devices. Whether it’s checking if you locked the front door, turning off appliances that were accidentally left on, or receiving alerts for potential issues like a water leak or an unexpected motion in your home, remote access ensures that you are always connected and in control. This proactive management capability not only saves energy and prevents potential mishaps but also provides invaluable peace of mind. The ability to monitor home security cameras, adjust thermostats, or even feed pets remotely has become a standard expectation for many, showcasing the profound impact of these remote IoT access examples on daily life.Business Imperatives: Ensuring Uptime and Usability
Beyond personal convenience, the implications of remote IoT access for businesses are monumental. Companies need a reliable, secure remote access and support solution to ensure the uptime and usability of all their IoT devices. This is because there is just too much money at stake to risk. From manufacturing floors to expansive agricultural fields, IoT devices are integral to critical operations. Downtime for these devices can lead to significant financial losses, disrupted supply chains, and damaged customer trust. Businesses require secure and reliable remote access and support solutions that make sure the uptime and usability of their IoT devices function effectively. Remote functionality in IoT also facilitates remote access to applications and systems, enabling users to remotely access files, databases, or software platforms. For instance, remote access allows employees to work from home or access critical business applications while traveling, ensuring business continuity and operational resilience. The financial impact of IoT device downtime can be catastrophic, making robust remote access solutions not just beneficial, but absolutely essential for modern enterprises.Real-World Remote IoT Access Examples Across Industries
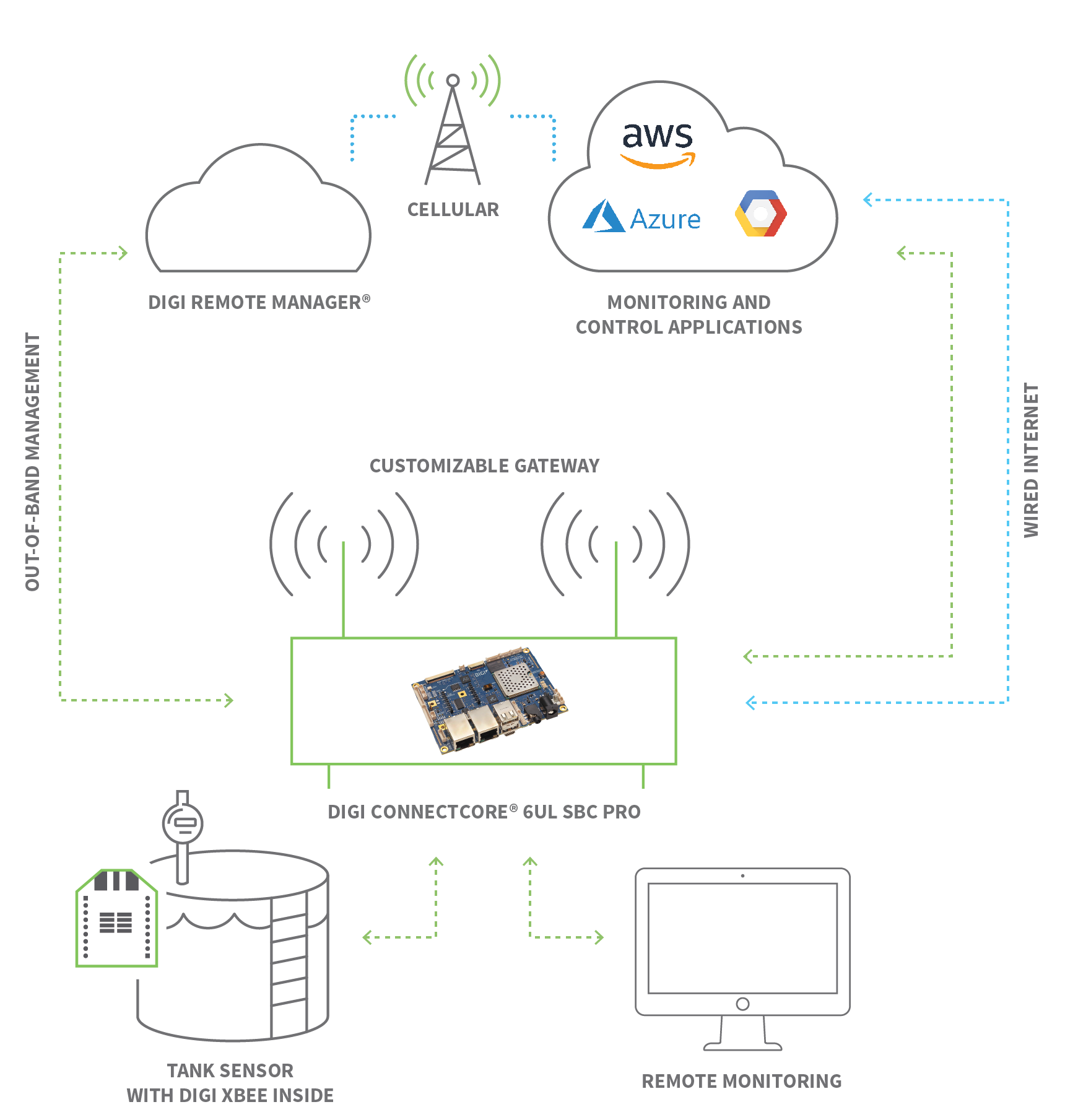
IoT opens doors to endless possibilities in industries like healthcare, agriculture, and transportation. The versatility of remote IoT access means its applications are incredibly diverse, spanning virtually every sector of the global economy. Let's explore some compelling remote IoT access examples that are already transforming various industries.Smart Homes and Personal Devices
The most familiar remote IoT access examples are often found within our homes. Smart thermostats like Nest or Ecobee allow you to adjust your home's temperature from your smartphone, saving energy when you're away and ensuring comfort upon your return. Smart lighting systems, such as Philips Hue, enable remote control over brightness and color, enhancing ambiance and security. Security cameras and doorbell systems (e.g., Ring, Arlo) provide live feeds and motion alerts directly to your phone, allowing you to monitor your property from anywhere. Even smart appliances, like refrigerators that alert you when you're low on milk or ovens that can be preheated on your commute home, exemplify the convenience offered by remotely accessing IoT devices. The ability to control and monitor your devices from anywhere empowers you to manage your environment, optimize energy usage, and stay connected to the things that matter most to you. These are just a few examples of the benefits of remote access to IoT devices.Retail Industry: Optimizing Operations and Customer Experience
Consider the retail industry as an example. In retail, IoT devices are used for inventory management, smart shelving, customer analytics, and point-of-sale (POS) systems. Remote access to these devices is crucial for maintaining seamless operations. Store managers can remotely monitor stock levels, adjust digital signage, troubleshoot malfunctioning POS terminals, or even manage smart security systems across multiple locations. This capability minimizes the need for on-site technicians, reduces operational costs, and ensures that stores are always ready to serve customers. For instance, if a digital display screen in a remote store malfunctions, an IT team can remotely diagnose and often fix the issue without dispatching personnel, saving time and money. The efficiency gained from such remote IoT access examples directly impacts the bottom line, highlighting why businesses require secure and reliable remote access and support solutions.Logistics and Supply Chain: A Growing Frontier
The logistics and supply chain sector is undergoing a massive transformation powered by IoT. As per a newly conducted study, the deployment of IoT technology in the global supply chain market is forecasted to grow at a CAGR of 13.2 percent between the years 2020 to 2030. Besides, the supply chain divisions that will enjoy significant benefits include fleet management, warehouse automation, and asset tracking. Remote IoT access in logistics means companies can monitor the real-time location and condition of goods in transit using GPS trackers and environmental sensors. If a refrigerated container experiences a temperature deviation, alerts can be sent instantly, allowing for remote adjustments or intervention to prevent spoilage. Fleet managers can remotely monitor vehicle diagnostics, optimize routes, and even perform over-the-air software updates on connected trucks. This level of remote oversight enhances efficiency, reduces waste, and improves overall supply chain resilience. These remote IoT access examples are vital for ensuring the timely and safe delivery of goods, especially in complex global networks.Healthcare, Agriculture, and Beyond
The impact of remote IoT access extends far beyond homes and retail. In healthcare, remote patient monitoring devices allow doctors to track vital signs, glucose levels, or heart activity of patients from a distance, enabling proactive care and reducing hospital readmissions. This is particularly crucial for chronic disease management or for elderly patients living independently. In agriculture, smart sensors monitor soil moisture, nutrient levels, and crop health, enabling farmers to optimize irrigation and fertilization remotely, leading to better yields and reduced resource consumption. Livestock tracking devices provide insights into animal health and location. In smart cities, remote access to streetlights, waste management systems, and public safety cameras allows for efficient urban management. These diverse remote IoT access examples underscore the technology's broad applicability and its potential to solve complex challenges across various domains.The Critical Risks of Neglecting Remote IoT Device Access
While the benefits of remote IoT access are undeniable, the risks of neglecting remote IoT devices access are profound and multifaceted. There is simply too much money at stake to leave them at risk. The cost of IoT device downtime can be astronomical for businesses, leading to direct financial losses, reputational damage, and even safety hazards. Consider a smart factory where IoT sensors monitor machinery performance. If remote access to these sensors is compromised or unavailable, a critical machine failure might go unnoticed until it's too late, leading to costly production halts, damaged equipment, and missed deadlines. In the retail sector, if POS systems or digital signage cannot be remotely managed or updated, stores could face operational paralysis, leading to lost sales and frustrated customers. Beyond operational disruptions, security vulnerabilities are a major concern. Unsecured remote access points can become gateways for cybercriminals to infiltrate networks, steal sensitive data, or even launch ransomware attacks. Imagine a scenario where a hacker gains control of a building's smart HVAC system, causing extreme temperatures, or worse, disabling security cameras. The potential for misuse, data breaches, and service disruptions highlights why secure and reliable remote access is not just a convenience, but a critical security imperative. Neglecting these risks is akin to leaving a business's most valuable assets exposed.Ensuring Security: Essential Protocols for Remote IoT Access
Given the significant risks, ensuring secure access to these devices remotely is crucial. That’s precisely where robust security protocols come into play. Several popular protocols facilitate remote access to IoT devices, each with its strengths and use cases. Here are some widely used protocols for remotely accessing IoT devices, ensuring that data integrity and device control are maintained. * **SSH (Secure Shell):** SSH is a cryptographic network protocol for operating network services securely over an unsecured network. It is widely used for remote command-line access, remote execution of commands, and secure file transfers. But with SSH IoT remotely example techniques, it’s not only possible but also secure. Administrators can execute commands, transfer files, and troubleshoot issues on IoT devices as if they were physically present, all while encrypting the communication to prevent eavesdropping and tampering. * **VPN (Virtual Private Network):** A VPN creates a secure, encrypted tunnel over a public network, allowing devices to connect to a private network as if they were physically located within it. This is an excellent solution for businesses with multiple IoT devices that need to be part of a secure internal network. It ensures that all traffic to and from the IoT devices is encrypted and routed securely, bypassing public internet vulnerabilities. * **MQTT (Message Queuing Telemetry Transport):** While primarily a messaging protocol for lightweight data transfer between devices, MQTT is often used in conjunction with other protocols for remote access. It enables devices to publish data to a central broker and subscribe to data from other devices. This allows for remote monitoring and control commands to be sent efficiently, especially in environments with limited bandwidth or intermittent connectivity. * **HTTPS/RESTful APIs:** For web-enabled IoT devices, HTTPS (HTTP Secure) combined with RESTful APIs (Application Programming Interfaces) provides a secure way to interact with devices over the internet. This is common for consumer-grade smart home devices where users interact with a web interface or mobile app that communicates with the device via cloud services. HTTPS encrypts the data, and API keys or tokens provide authentication. * **CoAP (Constrained Application Protocol):** Designed for constrained devices and networks, CoAP is a specialized web transfer protocol for use with constrained nodes and networks in the Internet of Things. It's similar to HTTP but optimized for low-power, low-bandwidth environments, making it suitable for direct device-to-device communication in some remote access scenarios, often secured with DTLS (Datagram Transport Layer Security). The choice of protocol depends on the specific requirements of the IoT deployment, including security needs, device capabilities, network conditions, and the type of data being exchanged. A layered security approach, combining these protocols with strong authentication, authorization, and encryption, is essential for truly secure remote IoT access.Setting Up Remote Access for Your IoT Devices
Now that we understand the different remote access methods available, let’s move on to the steps involved in setting up remote access for your IoT devices. Setting up remote access for your IoT devices may vary depending on the specific device and manufacturer, as well as the chosen protocol. However, here are some general steps to guide you through the process: 1. **Understand Your Device's Capabilities:** Before anything else, check your IoT device's documentation. Does it support remote access natively? What protocols does it use (e.g., MQTT, HTTP, SSH)? Some devices come with built-in cloud connectivity, simplifying the process. 2. **Network Configuration:** * **Static IP Address (Optional but Recommended):** Assigning a static IP address to your IoT device on your local network can make it easier to locate and connect to consistently. * **Port Forwarding (for direct access):** If you're using a direct connection method like SSH or a custom application, you might need to configure port forwarding on your router. This directs incoming traffic from a specific port on your public IP address to your IoT device's local IP address and port. *Caution: This can expose your device to the internet and should only be done with strong security measures in place.* * **VPN Setup:** For more secure and scalable solutions, setting up a VPN server on your network (either on your router or a dedicated device) allows you to securely connect to your entire home or business network, including your IoT devices, from anywhere. 3. **Choose a Remote Access Solution/Platform:** * **Cloud-based IoT Platforms:** Many IoT devices integrate with cloud platforms (e.g., AWS IoT, Google Cloud IoT Core, Microsoft Azure IoT Hub). These platforms provide secure, scalable ways to manage, monitor, and control devices remotely without direct port forwarding. They handle authentication, authorization, and data routing. * **Third-Party Remote Access Software:** Solutions like TeamViewer IoT, Remote.It, or dedicated IoT remote access tools offer secure tunnels and management interfaces, often bypassing complex network configurations like NAT router or firewall restrictions. * **DIY Solutions (e.g., SSH, VPN):** For more advanced users or specific use cases, setting up your own SSH server or VPN can provide granular control. This often requires more technical expertise. 4. **Security Measures:** This is paramount. * **Strong Passwords:** Always change default passwords to strong, unique ones. * **Two-Factor Authentication (2FA):** Enable 2FA wherever possible for an extra layer of security. * **Encryption:** Ensure all remote communication is encrypted (e.g., using HTTPS, SSH, VPN). * **Firewall Rules:** Configure firewalls to restrict access to only necessary ports and trusted IP addresses. * **Regular Updates:** Keep your device firmware and remote access software updated to patch security vulnerabilities. 5. **Testing:** After setup, thoroughly test your remote access. Try connecting from different networks (e.g., mobile data, a friend's Wi-Fi) to ensure connectivity and functionality. Verify that all controls and monitoring features work as expected. Remember, the goal is to balance convenience with robust security. Always prioritize security when setting up remote access for your IoT devices, especially when sensitive data or critical operations are involved.Overcoming Challenges in Remote IoT Connectivity
Despite the immense benefits, establishing reliable and secure remote IoT access isn't without its challenges. Network complexities, security concerns, and scalability issues often arise. One significant hurdle is dealing with network address translation (NAT) routers and firewall restrictions. Most home and business networks use NAT, which translates private IP addresses to a single public IP address, making it difficult to initiate direct connections to devices within the private network from the outside. Traditional methods like port forwarding can be cumbersome, insecure, and often blocked by ISPs or corporate firewalls. This is where modern remote access solutions come into play. Using our remote access solution, you can safely connect to a device on a private or mobile network, regardless of NAT router or firewall restrictions. These solutions often employ techniques like reverse tunnels or cloud-based relays to establish connections without requiring direct inbound port access. Another challenge is ensuring consistent connectivity, especially for mobile or intermittently connected devices. IoT devices might operate in environments with unreliable Wi-Fi, limited cellular coverage, or power constraints. Robust remote access solutions must be designed to handle these fluctuations, queue commands, and synchronize data when connectivity is restored. Finally, the sheer diversity of IoT devices and their underlying operating systems and protocols presents a compatibility challenge. A universal remote access solution must be flexible enough to support a wide array of devices, from simple sensors to complex industrial controllers, ensuring seamless integration and management. Overcoming these technical hurdles is key to unlocking the full potential of remote IoT access.The Future Landscape of Remote IoT Access
The trajectory of remote IoT access points towards an even more integrated, intelligent, and autonomous future. We are moving beyond simple remote control to predictive maintenance, AI-driven automation, and hyper-personalized experiences. Edge computing will play an increasingly vital role, allowing more data processing to occur closer to the IoT devices themselves, reducing latency and bandwidth requirements for remote operations. This means faster responses and more resilient systems, even when central cloud connectivity is limited. Furthermore, advancements in 5G technology will provide the high-speed, low-latency, and massive connectivity needed for widespread and reliable remote IoT deployments, particularly in critical applications like autonomous vehicles and remote surgery. Security will continue to be a paramount concern, with a growing emphasis on zero-trust architectures, blockchain for secure device identity, and advanced threat detection using machine learning. The focus will shift from merely securing connections to securing the entire IoT ecosystem, from device manufacturing to data lifecycle management. Ultimately, the future of remote IoT access will be characterized by greater intelligence, seamless interoperability, and an even deeper integration into the fabric of our daily lives and industrial operations. It will enable smarter cities, more efficient industries, and healthier, more connected individuals, constantly pushing the boundaries of what's possible in a hyper-connected world.Conclusion
In conclusion, remotely accessing IoT devices offers unparalleled convenience, enabling users to control and monitor their gadgets from anywhere in the world. As we have explored through various remote IoT access examples, this technology is not just about personal comfort but is a critical enabler for businesses across industries, from retail and logistics to healthcare and agriculture. The financial stakes are high, and the cost of neglecting secure, reliable remote access solutions can be devastating, making robust security protocols and well-planned implementation essential. The ability to connect, manage, and troubleshoot devices remotely ensures operational uptime, enhances efficiency, and unlocks new possibilities for innovation and service delivery. While challenges like network complexities exist, modern solutions are continually evolving to overcome them, paving the way for a more connected and intelligent future. We encourage you to consider how remote IoT access can benefit your personal life or business operations. Explore the various solutions available, prioritize security, and embrace the transformative power of being connected, always. Share your thoughts in the comments below – what remote IoT access examples have you found most impactful?
Best Remote IoT Device Management Platform Examples: Your Ultimate Guide

How To Achieve IoT Remote Access Behind Firewall Example: A
Remote IoT Device Platforms Examples: The Ultimate Guide For 2023