Securely Connect Your Devices: A Comprehensive Guide
In our increasingly interconnected world, the ability to connect devices securely is not just a convenience, but a fundamental necessity. From the smartphones in our pockets to the smart appliances in our homes, and the complex networks powering businesses, every connection presents a potential vulnerability. Protecting your digital life, your sensitive information, and your privacy hinges on understanding and implementing robust security practices for all your connected devices.
This article delves into the best practices for connecting devices securely, offering practical advice and insights to help you build a safe and resilient digital environment. We will explore foundational security measures, delve into remote access solutions, and examine the unique challenges and opportunities presented by the burgeoning Internet of Things (IoT). By the end, you'll be equipped with the knowledge to navigate the digital landscape with greater confidence, ensuring your valuable—and in some cases, priceless—content remains safe.
Table of Contents
- Why Secure Device Connections Matter More Than Ever
- Foundational Security: Protecting Your Devices at the Source
- Securely Connecting Devices in a Home or Office Network
- Remote Access: Connecting Devices Securely from Anywhere
- The Internet of Things (IoT): Securing a New Frontier
- Meshnet: Your Private, Versatile Network Solution
- Best Practices for Maintaining a Secure Digital Environment
- The Future of Secure Device Connectivity
Why Secure Device Connections Matter More Than Ever
In our interconnected world, the importance of securely connecting devices cannot be overstated. Whether it's smartphones, laptops, IoT devices, or home networks, securing these connections is vital to protect sensitive information and ensure smooth operation. Every piece of data, from personal photos and financial records to confidential business documents, traverses these connections. An insecure link can become an open door for cybercriminals, leading to data breaches, identity theft, financial fraud, and significant disruptions to your daily life or business operations.
The digital landscape is constantly evolving, with new threats emerging alongside new technologies. The sheer volume and variety of devices we use daily mean that the attack surface for malicious actors is continually expanding. This makes understanding how to securely connect devices not just a technical skill, but a critical life skill for anyone navigating the modern digital age. Protecting your digital assets starts with a proactive approach to security, ensuring that every connection you make is as robust and impenetrable as possible. Without this vigilance, the convenience of connectivity can quickly turn into a significant liability, underscoring why secure device connections are paramount.
Foundational Security: Protecting Your Devices at the Source
Before considering how devices interact with networks, it's crucial to establish a strong security posture at the device level itself. This forms the bedrock of your overall digital defense. By taking advantage of your device’s inherent security features and understanding the underlying network protocols, you can significantly reduce vulnerabilities and connect devices securely from the ground up.
Device-Level Security Features
Your devices come equipped with a range of security features designed to protect your data. The first step is to set up these security features diligently. This includes enabling encryption, which scrambles your data so that only authorized parties can read it, and setting up a robust passcode lockout. A strong, unique passcode or biometric authentication (like fingerprint or facial recognition) adds another crucial layer of protection to your device. This simple step can prevent unauthorized access to your valuable content, which in some cases can be priceless.
Beyond initial setup, consider the unfortunate event that you lose your device or if someone steals it. Modern devices offer capabilities that can mitigate the damage. You may be able to remotely "brick" your device to keep a stranger from breaking into your accounts. Bricking a device means remotely wiping a connected device and rendering it unusable. This ensures that even if the physical device is compromised, your sensitive data and accounts remain safe from unauthorized access, providing peace of mind in stressful situations.
Understanding Network Security Standards
When connecting to Wi-Fi networks, the security standard in use is paramount. WPA3 provides stronger security and is the latest standard for most modern networks, providing robust encryption. It provides stronger security than the older versions, WPA2 or WPA. Older routers often use WPA and WEP, which are outdated and not secure. Connecting to networks using these older standards significantly increases your risk of eavesdropping and data interception. Always prioritize WPA3-enabled networks whenever possible.
Another powerful, yet often overlooked, network security feature is MAC address filtering. Each device has a unique MAC address. By enabling MAC address filtering on your router, you can control which devices are allowed to connect to your network. This acts as an access control list, preventing unauthorized devices from easily connecting to your network even if they manage to guess your Wi-Fi password. While not foolproof, it adds an extra layer of defense. Additionally, while WPS (Wi-Fi Protected Setup) uses advanced security protocols to ensure that your network remains secure, it has historically been associated with vulnerabilities. If using WPS, ensure your router's firmware is updated and consider disabling it if not actively needed to prevent potential exploits.
Securely Connecting Devices in a Home or Office Network
Beyond individual device security, how you manage connections within your local network, be it at home or in an office, is critical. This involves understanding user permissions, managing device discovery, and leveraging specific tools designed for secure network integration. Ensuring these aspects are properly configured helps to connect devices securely and maintain network integrity.
For instance, within a Windows environment, managing user accounts is a fundamental security practice. Using the device you would like to connect, you can go to Windows Settings > Accounts > Family & other users (just "Other users" in Windows 11). Under "Family & other users," you can select an existing family member or select "Add a family member" or "Add account." Once they sign in, this device will appear as a managed entity, allowing for better oversight and control over who accesses what resources on your network. This is particularly useful for shared family computers or small office setups.
When it comes to wireless connections like Bluetooth, understanding discoverability is key. Once a device is discoverable, the *other* device (usually the one with a screen, like your phone or computer) needs to scan for available Bluetooth devices nearby. While convenient, leaving devices in a discoverable state for extended periods can expose them to unauthorized connection attempts. Always limit discoverability to only when necessary and pair devices in a secure, private environment. For more complex enterprise environments, tools like Cisco Network Setup Assistant, a Chrome extension, enable the secure connection of devices to networks using Cisco Identity Services Engine, providing centralized control and robust authentication for large-scale deployments.
Remote Access: Connecting Devices Securely from Anywhere
The ability to access devices and data remotely has become indispensable in our modern, mobile world. However, remote access inherently introduces new security challenges. Ensuring that these connections are secure is paramount to prevent unauthorized access to your home or work networks. This section explores various solutions designed to connect devices securely, regardless of physical location.
The Power of VPNs and Secure Tunnels
Virtual Private Networks (VPNs) are a cornerstone of secure remote access. VPNs create private access tunnels that connect devices to the same network irrespective of location. This means your data travels through an encrypted tunnel, making it virtually impossible for third parties to intercept or read. Secure Connect acts as your secure onramp to the internet and provides the first line of defense, encrypting your traffic from your device to the VPN server, and often beyond.
Solutions for remote access include OpenVPN and Layer Two Tunneling Protocol (L2TP). These are cryptographic systems that allow for secure remote connections even over unsecured or public networks, such as public Wi-Fi hotspots. By routing your traffic through a secure VPN server, your actual IP address is masked, and your data is protected, ensuring that you can connect devices securely without compromising your personal data or privacy, even when you're on the go.
Advanced Remote Solutions for Specific Needs
Beyond general VPNs, specialized tools cater to specific remote access requirements. For Windows environments, you can use the Windows app to securely connect remotely to your Windows devices and apps from Azure Virtual Desktop, Windows 365 Cloud PCs, Microsoft Dev Box, and Remote Desktop. These solutions provide a secure, managed way to access your desktop environment and applications as if you were sitting right in front of them, crucial for remote workforces and cloud-based operations.
For IT or customer service teams who need secure access to user devices, Virtual Network Computing (VNC) is a common choice. Many users can connect to a VNC instance, regardless of their operating system. VNC allows for remote control of a desktop interface, enabling support staff to troubleshoot issues directly. While powerful, VNC implementations must be secured with strong passwords and encryption to prevent unauthorized access. The key is to ensure that any remote access solution, whether it's for personal use or professional support, adheres to the highest security standards to protect the integrity of the connected devices and the data they hold.
The Internet of Things (IoT): Securing a New Frontier
The proliferation of IoT devices, from smart thermostats to industrial sensors, has brought immense convenience and efficiency. However, these devices often present unique security challenges due to their diverse nature, limited processing power, and sometimes, lax security implementations. Ensuring you can connect devices securely within the IoT ecosystem is vital for protecting your home, business, and personal data.
At the core of secure IoT connectivity lies device identity. A device can't connect to a hub unless it has a device identity. The IoT Hub Identity Registry, for example, only stores device identities to enable secure access to the IoT Hub. It stores device IDs and keys to use as security credentials, and an enabled/disabled flag that you can use to disable access for an individual device. This granular control is essential for managing a large fleet of devices and revoking access if a device is compromised or no longer needed.
Cloud providers also offer secure entry points for IoT devices. The device gateway is the entry point for devices to securely connect to AWS IoT Core, a managed cloud platform that enables connected devices to interact with cloud applications and other devices. This gateway handles authentication and authorization, ensuring that only legitimate devices can send and receive data. For more advanced users and specific applications, securely connecting remote IoT devices using P2P SSH on a Raspberry Pi is a powerful solution that can transform how you manage your networks. This allows you to do things like remotely control your IoT devices, transfer files securely, and even access the Raspberry Pi's desktop environment, offering a robust and flexible way to interact with your smart infrastructure.
Meshnet: Your Private, Versatile Network Solution
In the quest to connect devices securely and efficiently, innovative solutions like Meshnet are emerging as powerful alternatives to traditional networking paradigms. Meshnet is your secure and private network that serves multiple purposes, offering a flexible and user-friendly way to manage your digital connections.
For example, Meshnet lets you connect devices, reroute traffic, and use native remote access apps to log into your device or grab a file regardless of where you are. This capability is incredibly useful for individuals and small teams who need to access resources across different locations without the complexity of traditional VPN setups. Whether you want to share files, play LAN games with friends who are physically distant, or simply access other devices directly, Meshnet provides a streamlined and secure pathway.
It's designed to be fast, free, and friendly, making it accessible to a wide range of users. By creating a direct, encrypted connection between your devices, Meshnet bypasses the need for central servers or complex configurations, offering a truly peer-to-peer secure network. This decentralized approach enhances privacy and reduces potential points of failure, empowering users to connect their world in a way that is both secure and remarkably intuitive. Download today to experience a new level of secure and direct device connectivity.
Best Practices for Maintaining a Secure Digital Environment
Beyond specific technologies and tools, a consistent commitment to best practices is essential for maintaining a secure digital environment and ensuring you can always connect devices securely. These practices form a continuous cycle of vigilance and adaptation against evolving threats.
- Regular Software Updates: Always keep your operating systems, applications, and device firmware updated. Updates often include critical security patches that fix newly discovered vulnerabilities. Ignoring updates leaves your devices exposed to known exploits.
- Strong, Unique Passwords: Use complex, unique passwords for every account and device. Avoid easily guessable information. A password manager can help you generate and store these securely.
- Enable Two-Factor Authentication (2FA): Wherever possible, enable 2FA. This adds an extra layer of security by requiring a second form of verification (like a code from your phone) in addition to your password, making it much harder for unauthorized users to gain access even if they steal your password.
- Network Segmentation: For home and office networks, consider segmenting your network. For instance, create a separate guest Wi-Fi network or an isolated network for your IoT devices. This prevents a compromised IoT device from gaining access to your main network where sensitive data resides.
- Be Wary of Public Wi-Fi: Public Wi-Fi networks are often unsecured. If you must use them, always use a VPN to encrypt your traffic and avoid accessing sensitive accounts or performing financial transactions.
- Regular Security Audits and Monitoring: Periodically review your network settings, connected devices, and security logs. Look for unusual activity or unauthorized devices. Tools can help monitor network traffic for suspicious patterns.
- Educate Yourself: Stay informed about the latest cybersecurity threats and best practices. A knowledgeable user is the first and most effective line of defense against cyberattacks.
Adhering to these principles creates a robust defense, allowing you to confidently connect devices securely and protect your digital footprint.
The Future of Secure Device Connectivity
As technology advances, so too does the complexity of securing our interconnected world. The future of secure device connectivity is likely to be characterized by even more sophisticated security protocols, driven by innovations in artificial intelligence and machine learning. We can expect to see a greater emphasis on "zero-trust" architectures, where no device or user is inherently trusted, regardless of their location, requiring continuous verification.
Edge computing, where data processing happens closer to the source, will also play a significant role, demanding new security paradigms for distributed systems. The integration of blockchain technology could offer decentralized and immutable identity management for devices, enhancing trust and transparency. Ultimately, the goal remains the same: to connect devices securely and seamlessly, ensuring that the benefits of connectivity are realized without compromising privacy, data integrity, or operational continuity. The ongoing evolution of threats will necessitate a dynamic and adaptive approach to security, making continuous learning and proactive measures more critical than ever.
In an era where our lives are increasingly intertwined with technology, the ability to connect devices securely is no longer optional—it is a fundamental requirement. From setting up basic device-level protections like encryption and passcodes, to leveraging advanced remote access solutions such as VPNs and specialized Windows apps, and understanding the unique security needs of IoT devices, every step you take fortifies your digital defenses. Solutions like Meshnet further empower you to create private, versatile networks that enhance both security and convenience.
By adopting best practices, staying informed about evolving threats, and utilizing the robust tools available, you can confidently navigate the complexities of our interconnected world. Your data, your privacy, and your peace of mind depend on it. We encourage you to review your current device and network security settings today, implement the recommendations discussed, and share this article with others who can benefit from this vital information. What steps are you taking to connect devices securely in your daily life? Share your thoughts in the comments below!
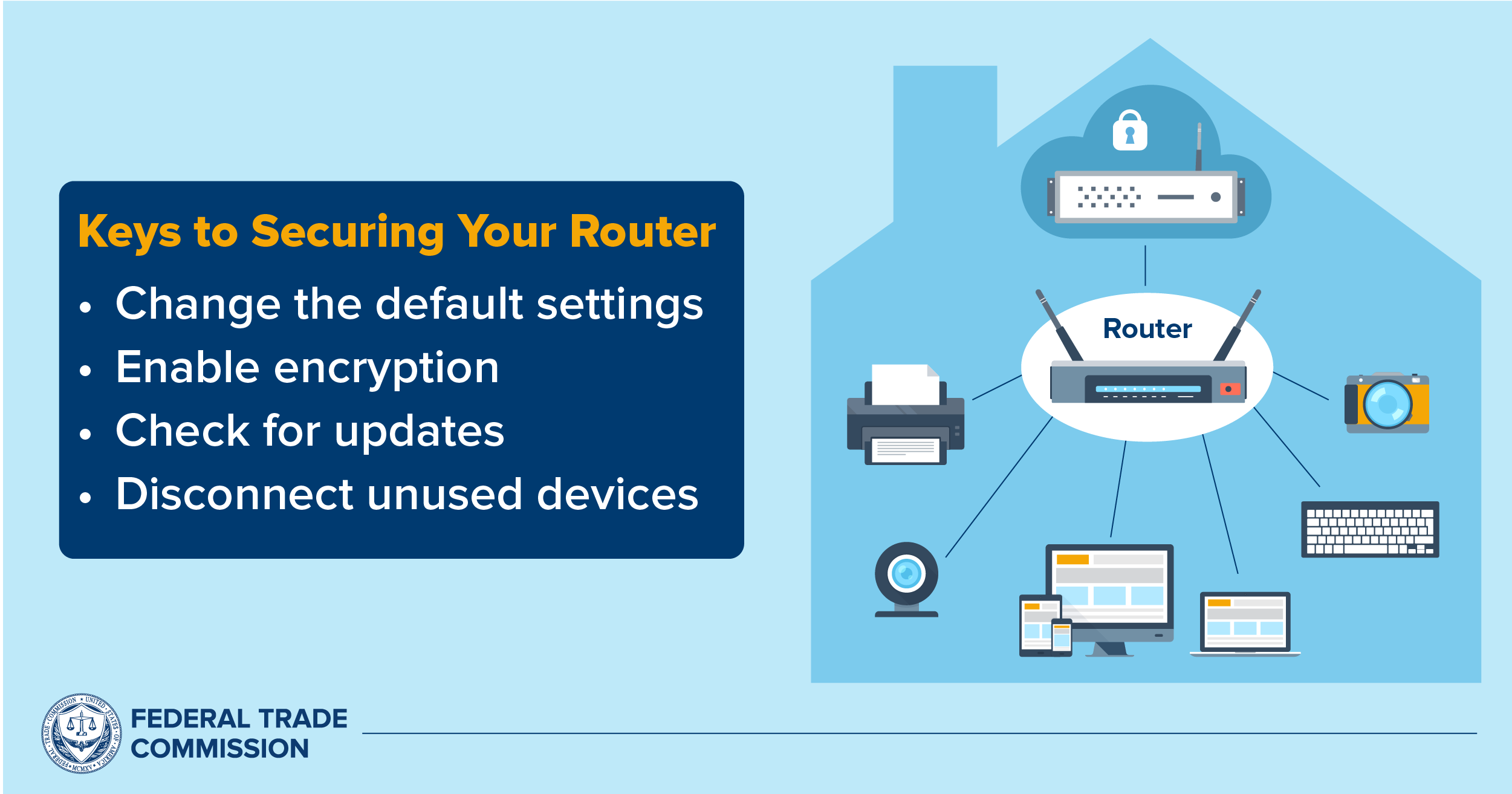
Securing Your Internet-Connected Devices at Home | Consumer Advice

Mastering Secure Connections: A Comprehensive Guide To Remotely

A guide to securely connecting IoT devices to the cloud - Embedded.com