Mastering Remote IoT Devices: Seamless Connectivity & Control
In today's interconnected world, the ability to interact with physical objects from afar has become not just a convenience, but a necessity. This is the essence of the Internet of Things (IoT), and at its core lies the concept of a remote IoT device. IoT remote access is the ability to connect to, monitor, and control Internet of Things (IoT) devices from a remote location. This capability is crucial for managing and supporting a wide array of IoT devices, such as smart appliances, industrial sensors, and connected vehicles, without needing to be physically present. But how exactly can one access IoT devices remotely, especially when they are behind complex network configurations like firewalls or NAT routers?
This comprehensive guide delves deep into the world of remote IoT devices, exploring the fundamental principles, practical methods, and critical considerations for effective management. From understanding the core technologies that enable remote connectivity to navigating the intricate landscape of security and scalability, we will equip you with the knowledge needed to harness the full potential of your IoT deployments. In this guide, we will uncover all about how to set up and establish an IoT remote SSH connection, alongside other vital remote access strategies.
Table of Contents
- The Transformative Power of Remote IoT Device Management
- Understanding IoT Remote Access: What It Is and Why It Matters
- Key Methods for Establishing Remote IoT Device Connectivity
- Step-by-Step: Setting Up Remote Access for Your IoT Devices
- Monitoring and Management: Keeping Your Remote IoT Devices Optimal
- Industry Applications: How Remote IoT Devices Drive Efficiency
- Navigating the Challenges of Remote IoT Device Management
- The Future Landscape of Remote IoT Devices
The Transformative Power of Remote IoT Device Management
The ability to manage and interact with a remote IoT device has revolutionized numerous sectors, from smart homes to heavy industry. Imagine adjusting the temperature in your home while you're still at work, or monitoring the performance of critical industrial equipment from a different continent. Remote access enables users to interact with their devices from anywhere, be it adjusting the temperature in their homes while at work or monitoring the performance of industrial equipment from a different location. This capability is not merely about convenience; it underpins significant operational efficiencies, cost reductions, and enhanced responsiveness. Businesses can deploy devices in hard-to-reach or geographically dispersed locations, knowing that they can still maintain full control and oversight without the prohibitive costs and logistical challenges of physical visits. For instance, a network of environmental sensors in remote wilderness areas can be monitored for data collection and health status updates, ensuring continuous operation and data integrity. This level of control is paramount for scaling IoT deployments effectively and extracting maximum value from connected ecosystems.Understanding IoT Remote Access: What It Is and Why It Matters
At its core, IoT remote access is the lifeline of any distributed IoT ecosystem. It encompasses the entire spectrum of connecting to, monitoring, and controlling IoT devices from a location other than their physical presence. This capability is not just a feature; it's a fundamental requirement for the viability and scalability of most IoT applications. Internet of Things device management is a list of processes that include equipping, validation, configuration, monitoring, and analysis of the connected devices in an IoT environment with the objective to give and support the spectrum of their functional abilities. Without robust remote access, managing a large fleet of smart meters, agricultural sensors, or even a network of smart streetlights would be an insurmountable task, demanding immense human resources and incurring significant operational costs. The importance of this capability cannot be overstated. It allows for proactive maintenance, enabling engineers to diagnose and often resolve issues before they escalate into critical failures. Real-time data monitoring ensures that devices are operating within optimal parameters, identifying anomalies that could indicate impending problems or security breaches. Furthermore, remote configuration and updates mean that devices can be adapted to new requirements or patched against vulnerabilities without the need for costly and time-consuming on-site visits. This dynamic management capability is what truly unlocks the potential of IoT, transforming raw data into actionable insights and maintaining the health of an entire connected infrastructure.Key Methods for Establishing Remote IoT Device Connectivity
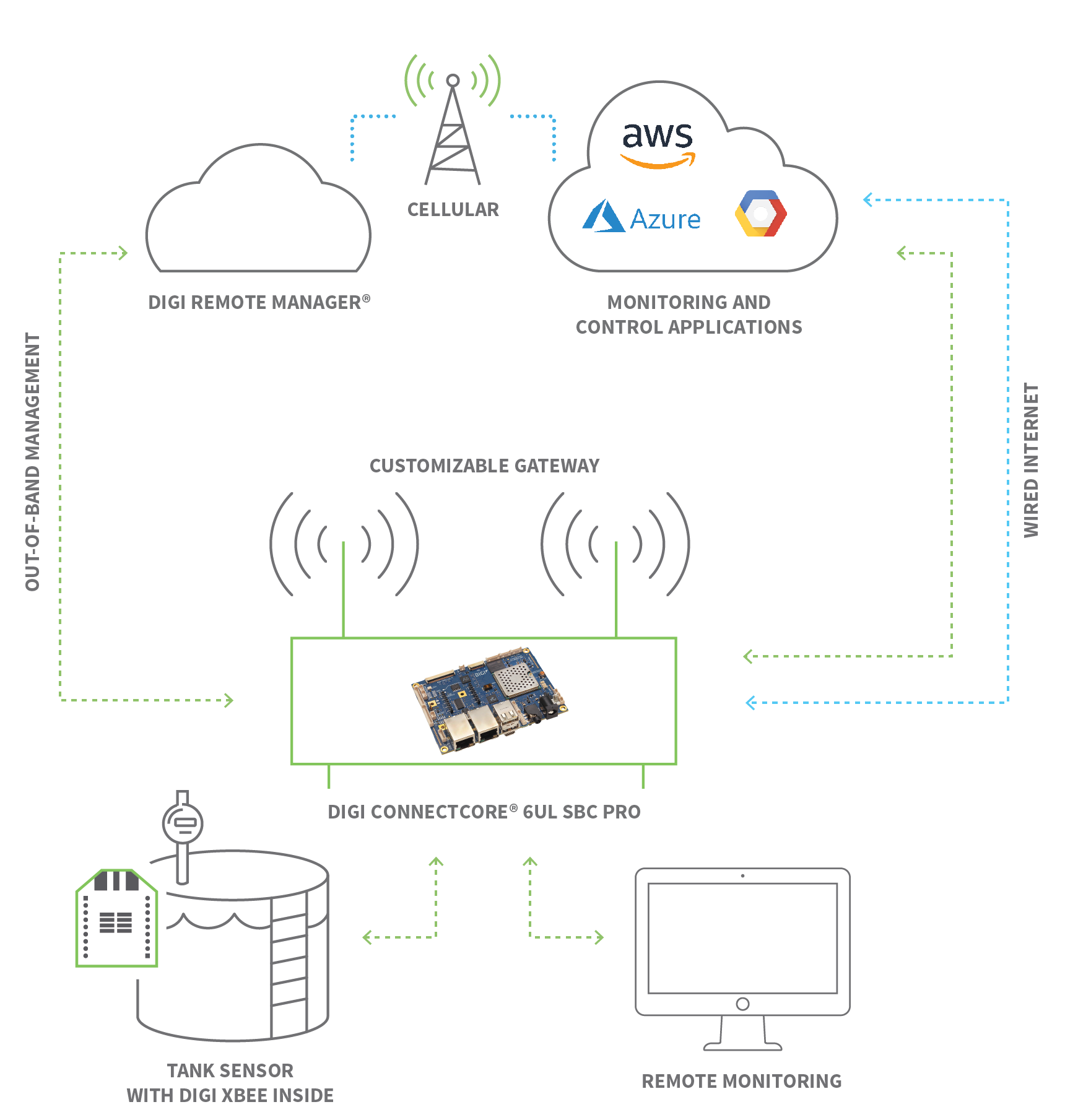
Establishing reliable and secure remote access to a remote IoT device is a multifaceted challenge, especially when devices are situated behind firewalls or NAT routers. Fortunately, several robust methods have emerged to address these complexities, each with its own advantages and ideal use cases. Understanding these approaches is crucial for designing a resilient and efficient IoT deployment.Secure Shell (SSH) for IoT Devices
When it comes to direct, command-line access to Linux-based IoT devices like Raspberry Pis, the Secure Shell (SSH) protocol stands out as a highly secure and versatile option. The secure shell (SSH) protocol is among the safest ways to gain remote access to IoT devices. SSH protects critical commands and data by enabling encrypted connection between users and distant equipment. This encryption is vital for protecting sensitive data and commands transmitted over potentially insecure networks. The primary challenge with SSH for remote IoT devices often arises when the device is behind a firewall or a Network Address Translation (NAT) router, common in home and industrial networks. Remotely SSH to IoT device behind firewall or NAT router typically requires techniques like port forwarding, reverse SSH tunnels, or using a jump host. These methods create a secure conduit through the network barriers, allowing you to establish an encrypted connection directly to your IoT device. SSH is invaluable for debugging, installing software, managing files, and performing system-level operations on your devices from anywhere in the world.Cloud-Based IoT Management Platforms
For large-scale deployments, managing individual SSH connections can quickly become impractical. This is where cloud-based IoT device management and remote access platforms come into their own. These platforms offer a centralized, scalable, and often user-friendly interface for managing an entire fleet of remote IoT devices. SocketXP is a cloud based IoT device management and remote access platform that exemplifies this approach, simplifying the complexities of network traversal and device orchestration. These platforms typically provide web dashboards, which are super handy when dealing with remote control IoT devices. They offer a unified and intuitive user experience for monitoring device status, pushing over-the-air (OTA) updates, configuring settings, and even debugging. Many IoT vendors like Rakwireless, Wanesy Management Center, and Gemtek have already managed to provide their customers with remote IoT device management platforms, recognizing the immense value they bring in streamlining operations. This compatibility streamlines device management, offering a unified and intuitive user experience across diverse device types and locations. They abstract away the underlying network complexities, allowing users to focus on device functionality and data.VPN and Other Network Solutions
Virtual Private Networks (VPNs) offer another robust method for establishing secure remote access by creating an encrypted tunnel between your remote location and the network where your IoT devices reside. Once connected to the VPN, your remote device essentially becomes part of the local network, allowing seamless access to all devices within that network, including your IoT fleet. This method is particularly useful for industrial settings where a secure, isolated network is preferred. Beyond VPNs, the underlying network technologies play a crucial role in enabling remote access. For devices deployed in areas without traditional wired internet, leveraging cellular, satellite, or hybrid network technologies is essential. Businesses can ensure their IoT deployments remain operational no matter the environment by leveraging cellular, satellite, or hybrid network technologies. These wireless solutions provide the necessary backbone for transmitting data and control commands to and from even the most geographically isolated remote IoT devices, ensuring continuous connectivity and operational continuity.Step-by-Step: Setting Up Remote Access for Your IoT Devices
Now that we understand the different remote access methods available, let’s move on to the steps involved in setting up remote access for your IoT devices. Setting up remote access for your IoT devices may vary depending on the specific device and manufacturer, as each might have its own quirks and preferred methods. However, here are some general steps to guide you through the process, with a focus on establishing robust and secure connections. **How to Set Up SSH for IoT Devices and Establish IoT Remote SSH Connections:** 1. **Prepare Your IoT Device:** * **Enable SSH:** Most Linux-based IoT devices (like Raspberry Pi) have SSH disabled by default for security. You'll need to enable it, often via a configuration tool (e.g., `raspi-config` for Raspberry Pi) or by creating a specific file (e.g., `ssh` file in the boot directory). * **Update and Upgrade:** Always ensure your device's operating system and software are up to date. This patches vulnerabilities and ensures compatibility. * **Static IP (Optional but Recommended):** Assigning a static IP address to your IoT device within its local network makes it easier to consistently locate it, especially if you're setting up port forwarding. 2. **Secure Your SSH Connection:** * **Change Default Credentials:** Immediately change the default username and password. This is a critical security step. * **Use SSH Key-Based Authentication:** This is far more secure than password authentication. Generate an SSH key pair on your local machine and copy the public key to your IoT device's `~/.ssh/authorized_keys` file. Disable password authentication once key-based authentication is working. * **Change SSH Port (Optional):** Moving SSH from its default port (22) to a non-standard port can deter automated scanning bots, though it's not a true security measure. 3. **Overcoming Network Barriers (Firewall/NAT Router):** * **Port Forwarding (Least Secure, Not Recommended for Public Internet):** If your IoT device needs to be directly accessible from the internet (e.g., for a web server), you can configure your router to forward a specific external port to the SSH port of your IoT device's internal IP address. This exposes your device to the internet and should be used with extreme caution and strong security measures. * **Reverse SSH Tunnel (More Secure):** This involves the IoT device initiating an SSH connection *outbound* to a publicly accessible server (your "jump host" or "bastion host"). This creates a tunnel that you can then use from your local machine to connect *back* to the IoT device through the jump host. This is excellent for devices behind NAT without router access. * **VPN:** Set up a VPN server on your local network or a dedicated VPN service. Your remote IoT device connects to this VPN, creating a secure tunnel. Once connected, your device is virtually on the same network as your local machine, allowing direct SSH access. * **Cloud-Based Tunneling Services:** Services like SocketXP, ngrok, or others provide secure tunnels without requiring router configuration or a public IP. The IoT device connects to their cloud service, and you connect to the cloud service, which then proxies your connection to the device. This is often the simplest and most secure method for individual devices. 4. **Test Your Connection:** * From your remote location, attempt to SSH into your IoT device using the chosen method. Verify that you can access the command line and execute commands. 5. **Implement Monitoring (Crucial for Remote Devices):** * Beyond just access, you'll want to monitor IoT device status and SD card health! Tools and scripts can be set up on the device to report back critical metrics, ensuring proactive management and preventing failures. By following these steps, you can establish a robust and secure remote access pipeline for your IoT devices, enabling effective management and troubleshooting from anywhere.Monitoring and Management: Keeping Your Remote IoT Devices Optimal
Establishing remote access is only the first step; continuous monitoring and proactive management are what truly ensure the longevity and effectiveness of your remote IoT device fleet. It's not enough to just connect; you need to know what's happening. The ability to monitor IoT device status and SD card health is paramount, as storage degradation or unexpected reboots can silently cripple an otherwise functional deployment. Effective IoT device management involves a comprehensive suite of processes, including equipping, validation, configuration, monitoring, and analysis of connected devices. This holistic approach aims to support the full spectrum of their functional abilities. Remotely manage, access and monitor your IoT devices, Raspberry Pi fleet or any Linux machines behind NAT router and firewall is the ultimate goal, allowing for real-time insights into performance, resource utilization, and potential issues. Modern IoT management platforms provide intuitive web dashboards that are super handy when dealing with remote control IoT devices. These dashboards aggregate data from various devices, presenting it in an easily digestible format. Key performance indicators (KPIs) like CPU usage, memory consumption, network connectivity, battery life, and sensor readings can be tracked. Alerts can be configured to notify administrators of deviations from normal operating parameters, enabling swift intervention. This proactive monitoring allows for predictive maintenance, where potential failures are identified and addressed before they impact operations, significantly reducing downtime and service disruptions. The continuous feedback loop from monitoring informs ongoing optimization and ensures that your remote IoT devices are always performing at their peak.Industry Applications: How Remote IoT Devices Drive Efficiency
The practical applications of remote IoT devices span an incredible breadth of industries, fundamentally transforming operations and enhancing customer service. This article describes how industries leverage remote IoT devices, and how controlling them helps with streamlining operations and makes customer service more efficient. The impact is profound, leading to significant improvements in productivity, safety, and profitability. In the **manufacturing sector**, remote IoT devices monitor production lines, predict machinery failures through real-time data analysis, and even allow for remote recalibration of equipment. This drastically reduces downtime and optimizes output. For **agriculture**, sensors deployed across vast fields can remotely monitor soil moisture, nutrient levels, and crop health, enabling precision farming that conserves resources and boosts yields. In **smart cities**, remote IoT devices manage traffic lights, monitor air quality, and control public lighting, leading to more efficient urban environments and improved public safety. The **healthcare industry** benefits from remote patient monitoring devices that transmit vital signs to medical professionals, allowing for continuous oversight and timely intervention without the need for constant physical presence. In **logistics and transportation**, connected vehicles and cargo sensors provide real-time tracking, temperature monitoring for perishable goods, and predictive maintenance for vehicle fleets, ensuring efficient delivery and reduced operational costs. Across all these sectors, the ability to remotely manage, access, and monitor these devices is the linchpin, enabling businesses to make data-driven decisions, automate processes, and provide unparalleled service to their customers.Navigating the Challenges of Remote IoT Device Management
While the benefits of remote IoT devices are undeniable, their management comes with a unique set of challenges that demand careful consideration. As businesses expand their IoT device count, they encounter a few common challenges that can hinder growth. These hurdles, if not adequately addressed, can undermine the very advantages that remote IoT promises, leading to security vulnerabilities, operational inefficiencies, and significant financial risks.The Critical Role of Security
Perhaps the most pressing challenge in remote IoT device management is security. Every IoT device is a potential gateway for malicious actors. Ensuring security in data connections and IoT hardware is paramount, as the consequences of a breach can range from data theft and system compromise to physical damage and safety hazards. The statistics are sobering: each week, 54% of organizations suffer from attempted cyber attacks targeting IoT devices, highlighting the pervasive nature of this threat. These attacks often exploit weak default passwords, unpatched vulnerabilities, or insecure communication protocols. This is why an effective and secure IoT device management solution is highly critical. It must incorporate end-to-end encryption, robust authentication mechanisms (like multi-factor authentication and certificate-based security), and regular security updates. Devices must be provisioned securely, and their communication channels hardened against eavesdropping and tampering. Furthermore, continuous monitoring for unusual activity and prompt incident response capabilities are essential. The interconnected nature of IoT means that a single compromised device can serve as a pivot point for attacks on an entire network, underscoring the need for a comprehensive, layered security strategy. Beyond security, other significant challenges include: * **Scalability:** Managing hundreds, thousands, or even millions of devices requires robust infrastructure and automated processes for provisioning, updating, and monitoring. Manual intervention becomes impossible at scale. * **Connectivity Reliability:** Devices in remote or challenging environments may experience intermittent connectivity. Solutions must be designed to handle offline periods, store-and-forward data, and automatically reconnect. * **Interoperability:** The IoT landscape is fragmented, with numerous protocols, standards, and vendors. Ensuring that diverse devices can communicate and be managed from a single platform is a complex task. However, this compatibility streamlines device management, offering a unified and intuitive user experience when achieved. * **Power Management:** Many remote IoT devices rely on batteries or limited power sources. Efficient power consumption is critical for long-term deployment without frequent maintenance. Addressing these challenges requires a strategic approach, leveraging advanced management platforms, adhering to best security practices, and designing for resilience from the ground up.The Future Landscape of Remote IoT Devices
The trajectory of remote IoT devices points towards an even more interconnected, intelligent, and autonomous future. Emerging technologies are set to redefine how we interact with and manage our connected world, pushing the boundaries of what's currently possible. One of the most significant trends is the integration of Artificial Intelligence (AI) and Machine Learning (ML) directly into remote IoT devices, often referred to as "edge AI." This allows devices to process data locally, make real-time decisions, and even learn from their environment without constantly communicating with the cloud. For instance, a remote industrial sensor could use AI to predict equipment failure with greater accuracy or optimize its own power consumption based on usage patterns. This reduces latency, conserves bandwidth, and enhances privacy. The rollout of 5G networks will also be a game-changer. Its ultra-low latency, massive connectivity, and high bandwidth capabilities will enable more sophisticated remote control scenarios, real-time video streaming from remote locations, and reliable communication for critical applications like autonomous vehicles and remote surgery. This robust connectivity will further solidify the foundation for truly pervasive IoT deployments. We can anticipate a future where remote IoT devices are not just managed but are self-managing, self-healing, and capable of complex collaborative tasks. Predictive maintenance will evolve into prescriptive maintenance, where devices not only flag potential issues but also recommend and even initiate corrective actions autonomously. The focus will shift from merely collecting data to deriving actionable intelligence at the source, leading to unprecedented levels of efficiency, safety, and innovation across every sector. The continuous evolution of remote IoT device capabilities promises a world where our physical environment is not just connected, but intelligently responsive to our needs.Conclusion
The journey through the world of remote IoT devices reveals a landscape brimming with potential and transformative power. We've explored how the ability to remotely manage, access, and monitor these devices is not just a
Best Remote IoT Device Management Platform Examples: Your Ultimate Guide
Remote IoT Device Platforms Examples: The Ultimate Guide For 2023

How Do I Access IoT Devices Remotely? | Robots.net