Connect IoT Device Remotely: Unlocking Global Control
In today's interconnected world, the ability to **connect IoT device remotely** has transitioned from a niche capability to an absolute necessity. The Internet of Things (IoT) has profoundly reshaped how we interact with technology, bringing unprecedented convenience and efficiency across various sectors. From smart homes to vast industrial complexes, IoT devices are constantly collecting data, automating tasks, and providing real-time insights. However, the true power of these devices is unleashed when you can access, monitor, and control them from anywhere in the world, transcending physical boundaries.
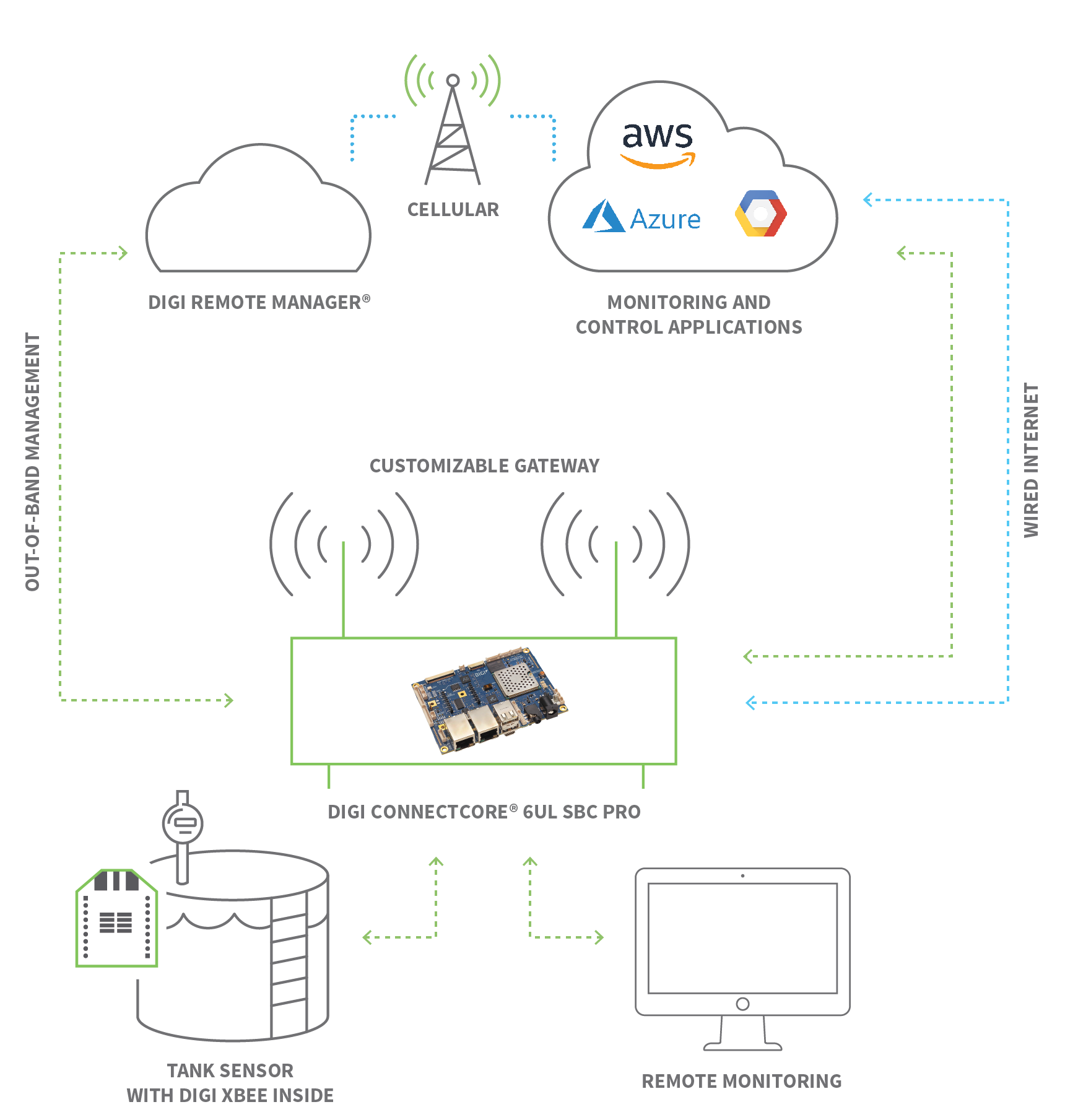
This capability, often referred to as IoT remote access, allows individuals and organizations to manage a wide array of IoT devices – such as smart appliances, sophisticated industrial sensors, and even connected vehicles – without needing to be physically present. Imagine troubleshooting a sensor in a remote oil rig from your office, or adjusting the climate control in your smart home while on vacation. This article will delve deep into the world of remote IoT connectivity, exploring its importance, the technologies that make it possible, and how you can securely set it up for your own devices.
Table of Contents
- What is Remote IoT Device Connectivity?
- Why is Remote Access Crucial for IoT Devices?
- Common Methods to Connect IoT Device Remotely
- Setting Up Remote Access for Your IoT Devices
- Advanced Solutions for Enterprise IoT Remote Management
- Security Best Practices for Remote IoT Access
- The Future of Remote IoT Connectivity
- Conclusion
What is Remote IoT Device Connectivity?
IoT remote access is fundamentally the ability to connect to, monitor, and control Internet of Things (IoT) devices from a remote location. This means you don't need to be physically next to your smart thermostat, industrial sensor, or connected vehicle to interact with it. Instead, you can use another computer or device, typically over the internet, to send commands, receive data, and manage its operations. The Internet of Things has become one of the most important technologies of the past decade, with IoT devices connecting to the internet through embedded systems, enabling seamless communication across vast distances.
This capability is crucial for managing and supporting a wide array of IoT devices. Whether it's a smart home appliance, a fleet of delivery drones, or environmental sensors deployed in remote areas, remote connectivity ensures continuous operation and responsiveness. The core idea is to extend your reach beyond the physical confines, allowing for unparalleled convenience and flexibility in how you interact with your connected world.
Why is Remote Access Crucial for IoT Devices?
The benefits and importance of remote access to IoT devices cannot be overstated, particularly for enterprises. It’s not just about convenience; it’s about operational efficiency, risk reduction, and unlocking new business opportunities. Remote control of devices using IoT offers unparalleled convenience and flexibility, allowing users to monitor, manage, and adjust IoT devices from any location with an internet connection.
Enhancing Operational Efficiency and Management
One of the primary advantages of being able to connect IoT device remotely is the significant enhancement in operational efficiency. It streamlines the management of IoT devices at scale, improving overall performance and reducing risks. Administrators can keep a constant eye on the performance and status of devices, proactively identifying and addressing issues before they escalate. This remote monitoring and management of devices is commonly used in various scenarios, from industrial automation to smart city infrastructure. Imagine a scenario where a critical sensor in a manufacturing plant starts reporting anomalies. With remote access, an engineer can immediately log in, diagnose the problem, and potentially even push a software fix without needing to travel to the site, saving valuable time and resources. This proactive approach minimizes downtime and ensures continuous operation, which is critical for many businesses.
Unlocking Global Reach and Flexibility
The ability to connect IoT device remotely truly globalizes your operations. With a VPN, for instance, you can access your IoT device from anywhere in the world, as long as you have an internet connection. Whether you’re in a different country or on the go, you can control and monitor your device as if you were physically present. This level of flexibility is transformative. For businesses with distributed assets or for individuals managing smart homes while traveling, it means constant control and peace of mind. It eliminates geographical barriers, allowing for centralized management of geographically dispersed IoT deployments. This global reach enhances your IoT device control and management from anywhere in the world, providing a competitive edge.
Driving Business Growth: The Logistics Example
Remote access to IoT devices offers significant benefits for enterprises, particularly in sectors like logistics. The deployment of IoT technology in the global supply chain market is forecasted to grow at a Compound Annual Growth Rate (CAGR) of 13.2 percent between the years 2020 to 2030, according to a newly conducted study. This growth is largely fueled by the capabilities that remote IoT access provides. In logistics, IoT devices can track shipments, monitor environmental conditions within containers, and manage vehicle fleets. Remote access allows logistics companies to:
- Monitor the real-time location and status of goods.
- Adjust refrigeration settings in cargo containers from a central office.
- Diagnose issues with vehicle telematics systems without physical intervention.
- Optimize routes and delivery schedules based on live data.
These capabilities lead to reduced operational costs, improved delivery times, enhanced security, and greater customer satisfaction, directly contributing to business growth and profitability. The number of connected devices for remote diagnostics, monitoring, and process control is expected to reach 96.7 thousand by 2026, further highlighting the growing importance of this technology.
Common Methods to Connect IoT Device Remotely
To effectively connect IoT device remotely, several techniques can be employed. The choice of method often depends on the specific requirements, the type of device, and the desired level of interaction. The most common protocols include Secure Shell (SSH), Virtual Network Computing (VNC), and Remote Desktop Protocol (RDP).
Secure Shell (SSH): The Gold Standard for Remote IoT
The Secure Shell (SSH) protocol is widely used for remotely accessing IoT devices because of its emphasis on encryption throughout the server connection process. This makes it an incredibly secure method for command-line access. Use of IoT remote SSH connection is particularly common in three main scenarios:
- Remote Monitoring and Management of Devices: This helps administrators to keep an eye on the performance and status of devices, execute commands, and manage configurations.
- Troubleshooting and Diagnostics: SSH allows engineers to delve into the device's operating system, check logs, and run diagnostic tools to pinpoint and resolve issues.
- Software Updates and Maintenance: Deploying patches, updating firmware, or installing new software packages can be done efficiently and securely over an SSH connection.
SSH provides a robust, encrypted tunnel, ensuring that all data exchanged between your remote computer and the IoT device remains confidential and protected from eavesdropping. This makes it ideal for sensitive operations on headless (no display) IoT devices like Raspberry Pi boards or industrial sensors.
VNC and RDP: Visual Remote Control
While SSH is excellent for command-line access, sometimes you need a graphical interface to manage your IoT device. This is where VNC (Virtual Network Computing) and RDP (Remote Desktop Protocol) come into play.
- VNC: VNC allows you to view and interact with the graphical desktop environment of your IoT device from a remote location. For example, users can set up a VNC server on a Raspberry Pi and use a VNC client application (like TightVNC) on a Windows or Mac laptop to view and interact with the Pi's desktop from anywhere with an internet connection. Before you can remotely connect to your IoT via VNC, you need to make sure your IoT is set up and running with a desktop environment (like XFCE desktop environment on IoT). This is particularly useful for devices that run a full operating system and require visual interaction, such as configuring software with a GUI or accessing web browsers on the device itself.
- RDP: Primarily used with Windows-based systems, RDP offers a rich graphical experience for remote control. While less common for typical Linux-based IoT devices, it's an option if your IoT device runs a Windows IoT Core or similar Windows variant.
Both VNC and RDP extend the remote control experience beyond the command line, offering a more intuitive way to manage devices that have a graphical user interface.
Setting Up Remote Access for Your IoT Devices
Now that we understand the different remote access methods available, let’s move on to the steps involved in setting up remote access for your IoT devices. Setting up remote access for your IoT devices may vary depending on the specific device and manufacturer. However, here are some general steps to guide you through the process.
Prerequisites for Remote IoT Access
Before you begin setting up your Linux server or any IoT device for remote access, there are a few prerequisites you need to consider:
- Compatible IoT Device: Ensure your device supports the remote access protocols you intend to use (SSH, VNC, RDP). Most modern IoT devices, especially development boards like Raspberry Pi, come with SSH enabled or easily configurable.
- Stable Internet Connection: Both your IoT device and the remote computer need a reliable internet connection.
- Power Supply: Ensure your IoT device has a stable power source for continuous operation.
- Basic Networking Knowledge: Understanding IP addresses, ports, and network configurations will be beneficial.
Compatibility and Firmware Check
The first crucial step is to check if your IoT devices are compatible with remote access protocols and verify if the devices have the required firmware or software that supports remote control. Many devices come with these capabilities built-in, but some may require specific firmware updates or software installations. Consult your device's documentation for details. For instance, a Raspberry Pi needs its SSH server enabled, which can usually be done through the `raspi-config` tool or by placing an empty `ssh` file in the boot directory of the SD card.
SSH Setup Example: Raspberry Pi or Linux Devices
Let's focus on how to remotely SSH Raspberry Pi or other Linux-based IoT devices. These devices connect to the internet through embedded systems, enabling seamless communication.
- Enable SSH on your IoT Device:
- For Raspberry Pi: Use `sudo raspi-config` -> Interface Options -> SSH -> Enable.
- For other Linux devices: Ensure `sshd` service is running (`sudo systemctl enable ssh --now`).
- Find your Device's IP Address: On your IoT device, open a terminal and type `hostname -I` or `ip a`. Note down the IP address (e.g., `192.168.1.100`). This is its local network IP.
- Access IoT Devices Remotely with SSH on Windows/Mac/Linux:
- On Windows: Install an SSH client like PuTTY, or use Windows Terminal (which has built-in SSH support).
- On Mac/Linux: Open your terminal.
- Connect: In your client or terminal, use the command: `ssh username@device_ip_address` (e.g., `ssh pi@192.168.1.100`). You'll be prompted for the password.
This allows you to establish an SSH connection to your devices from anywhere within your local network. To connect from outside your local network (over the internet), you typically need to configure port forwarding on your router, which can be complex and poses security risks if not done correctly.
Tunneling for Enhanced Security and No Port Forwarding
Learning how to securely connect to your Raspberry Pi or IoT device remotely over the internet without the need for port forwarding is a significant advantage. This is where secure tunneling solutions come into play. These services create an outbound connection from your IoT device to a public server, establishing a secure tunnel through which you can then access your device. This method bypasses the need for complex router configurations and often enhances security.
Explore methods such as SSH tunnels, and discover how to use services like pinggy.io to create secure tunnels for seamless remote management. For example, to create a tunnel to port 22 (SSH) using a service like Pinggy.io:
- On your IoT device, open a terminal or SSH client.
- Run a command similar to: `ssh -p 22 -R 0:localhost:22 tunnel_user@tunnel_server.com` (specific command will depend on the tunneling service). For Pinggy.io, it might be as simple as `ssh -p 22 -R 80:localhost:22 pinggy.io`.
This command creates a secure tunnel, making your local SSH port accessible via a public URL provided by the tunneling service. You can then use this public URL to connect to your device from anywhere, enhancing your IoT device control and management from anywhere in the world.
Advanced Solutions for Enterprise IoT Remote Management
For large-scale deployments and enterprise environments, specialized solutions offer more robust and scalable remote access capabilities. These platforms go beyond basic SSH or VNC, providing centralized management, advanced security features, and integration with existing IT infrastructure.
TeamViewer Tensor is a powerful and flexible solution that allows remote access to IoT devices easily and securely. With TeamViewer Tensor, you can manage, service, and support your IoT devices from anywhere at any time. It offers features like:
- Centralized Device Management: Oversee hundreds or thousands of devices from a single dashboard.
- Secure Connections: Built-in encryption and access controls.
- Remote Monitoring and Diagnostics: Real-time data and alerts.
- Scripting and Automation: Automate tasks across multiple devices.
- Integration Capabilities: Connects with other enterprise systems.
To learn more about TeamViewer Tensor and how it can help you unlock the full potential of IoT in your organization, exploring such dedicated platforms is highly recommended for businesses serious about scaling their IoT initiatives.
Security Best Practices for Remote IoT Access
While the ability to connect IoT device remotely offers immense benefits, it also introduces potential security vulnerabilities. Here are some frequently asked questions about IoT remote access using SSH, covering how it works, its security implications, and best practices for managing connected devices remotely:
- Use Strong Passwords and SSH Keys: Never use default passwords. Always set strong, unique passwords for your IoT devices. For SSH, using key-based authentication is far more secure than passwords. Generate an SSH key pair and disable password authentication.
- Change Default Ports: If you must use port forwarding, change the default SSH port (22) to a non-standard, high-numbered port. This reduces automated scanning attempts.
- Implement Firewall Rules: Configure your device's firewall (e.g., `ufw` on Linux) to only allow SSH connections from known IP addresses or specific networks.
- Regularly Update Firmware and Software: Keep your IoT device's operating system, firmware, and all installed software up to date. Updates often include critical security patches.
- Disable Unused Services: Minimize the attack surface by disabling any services or protocols on your IoT device that are not essential for its operation.
- Monitor Logs: Regularly check your device's logs for any suspicious activity or failed login attempts.
- Use VPNs or Secure Tunnels: As discussed, VPNs and tunneling services (like Pinggy.io) provide an encrypted, secure pathway to your devices, often negating the need for risky port forwarding.
- Implement Multi-Factor Authentication (MFA): Where possible, enable MFA for remote access portals or accounts.
Adhering to these best practices is paramount to ensure that your remote IoT connections remain secure and your devices are protected from unauthorized access or cyber threats.
The Future of Remote IoT Connectivity
The trajectory for remote IoT connectivity is one of continuous growth and increasing sophistication. As the number of connected devices explodes, so too will the demand for seamless, secure, and scalable remote management solutions. The forecast of 96.7 thousand connected devices for remote diagnostics, monitoring, and process control by 2026 underscores this trend.
Future developments will likely focus on:
- AI and Machine Learning Integration: For predictive maintenance and autonomous troubleshooting.
- Edge Computing: Processing data closer to the source, reducing latency and reliance on constant cloud connectivity.
- Enhanced Security Frameworks: More robust protocols and hardware-level security.
- Standardization: Efforts to create universal remote access standards for greater interoperability.
- User-Friendly Interfaces: Simplification of remote access setup and management, making it accessible to a broader audience.
The evolution of remote IoT platforms will continue to empower businesses and individuals to harness the full potential of their connected devices, driving innovation and efficiency across all aspects of life.
Conclusion
The ability to **connect IoT device remotely** is not just a technical feature; it's a fundamental enabler for the widespread adoption and success of the Internet of Things. From enhancing operational efficiency and providing unparalleled flexibility to driving significant business growth in sectors like logistics, remote access is an indispensable tool. We've explored the core concepts, delved into essential methods like SSH, VNC, and RDP, and outlined the practical steps for setting up secure remote connections, including the benefits of tunneling solutions.
As the IoT landscape continues to expand, the importance of secure, reliable, and efficient remote management will only intensify. By understanding the technologies involved and adhering to robust security best practices, you can unlock the full potential of your IoT devices, managing them effortlessly from anywhere in the world.
What are your experiences with remote IoT access? Share your thoughts and tips in the comments below, or explore more of our articles on IoT security and deployment strategies to further enhance your knowledge!

Mastering Secure Connections: A Comprehensive Guide To Remotely

Mastering Remote Access For IoT Devices On Your Mac
Remote IoT Device Platforms Examples: The Ultimate Guide For 2023