Securely Connect Remote IoT To AWS VPC: A Comprehensive Guide
In today's interconnected world, the proliferation of Internet of Things (IoT) devices has transformed industries and daily lives. From smart homes to industrial automation, these devices gather and transmit vast amounts of data. However, the convenience of remote access comes with a critical challenge: ensuring the security of the connection between your remote IoT devices, like a Raspberry Pi, and your central cloud infrastructure. Securing the connection between remote IoT devices like a Raspberry Pi and your AWS VPC is vital for protecting your data and preventing security breaches. This guide will delve into the best practices for securely connecting remote IoT devices within an AWS VPC environment, ensuring robust protection for your network.
For professionals, developers, and IT administrators, establishing a reliable and secure connection for their IoT devices within an AWS VPC is not just a best practice; it's a fundamental requirement. AWS Virtual Private Cloud (VPC) provides a secure and isolated environment for managing these devices, offering a robust foundation for your IoT ecosystem. Understanding how to establish a secure connection between your remote IoT setup and your AWS infrastructure is paramount for maintaining data integrity and operational continuity. This article is designed to provide a comprehensive solution to securely connect remote IoT devices, specifically a Raspberry Pi, to Amazon Web Services (AWS) using a Virtual Private Cloud.
Table of Contents:
- The Imperative of Secure IoT Connectivity
- Understanding Your AWS VPC for IoT
- Raspberry Pi: The Remote IoT Device
- Core Technologies for Secure IoT-VPC Connection
- Step-by-Step: Securely Connecting Remote IoT to AWS VPC
- Best Practices for Robust IoT Security in AWS
- Diagnosing and Troubleshooting Connection Issues
- Real-World Applications and Use Cases
The Imperative of Secure IoT Connectivity
The sheer volume of IoT devices deployed globally, from smart sensors in agricultural fields to automated machinery in factories, necessitates an unwavering focus on security. Each device represents a potential entry point for malicious actors if not properly secured. The data collected by these devices can be highly sensitive, ranging from personal health information to proprietary industrial processes. A security breach in an IoT ecosystem can lead to data theft, operational disruption, financial losses, and significant reputational damage. Therefore, securely connecting remote IoT devices to a robust cloud infrastructure like AWS VPC is not merely an option but a critical mandate for any organization or individual leveraging IoT technology.
The challenge lies in the distributed nature of IoT. Devices are often located in remote, uncontrolled environments, making traditional perimeter security measures difficult to apply. This distributed landscape demands a security model where each connection is inherently secure, authenticated, and encrypted. AWS VPC provides the ideal secure and isolated environment for managing these devices, acting as a digital fortress for your IoT data and applications. By establishing a secure connection between your remote IoT devices and your AWS VPC, you create a trusted pathway for data exchange, mitigating the risks associated with public internet exposure. This guide navigates the intricate landscape of securely connecting remote IoT devices to an AWS virtual private cloud (VPC), specifically focusing on leveraging Raspberry Pi as a common edge device.
Understanding Your AWS VPC for IoT
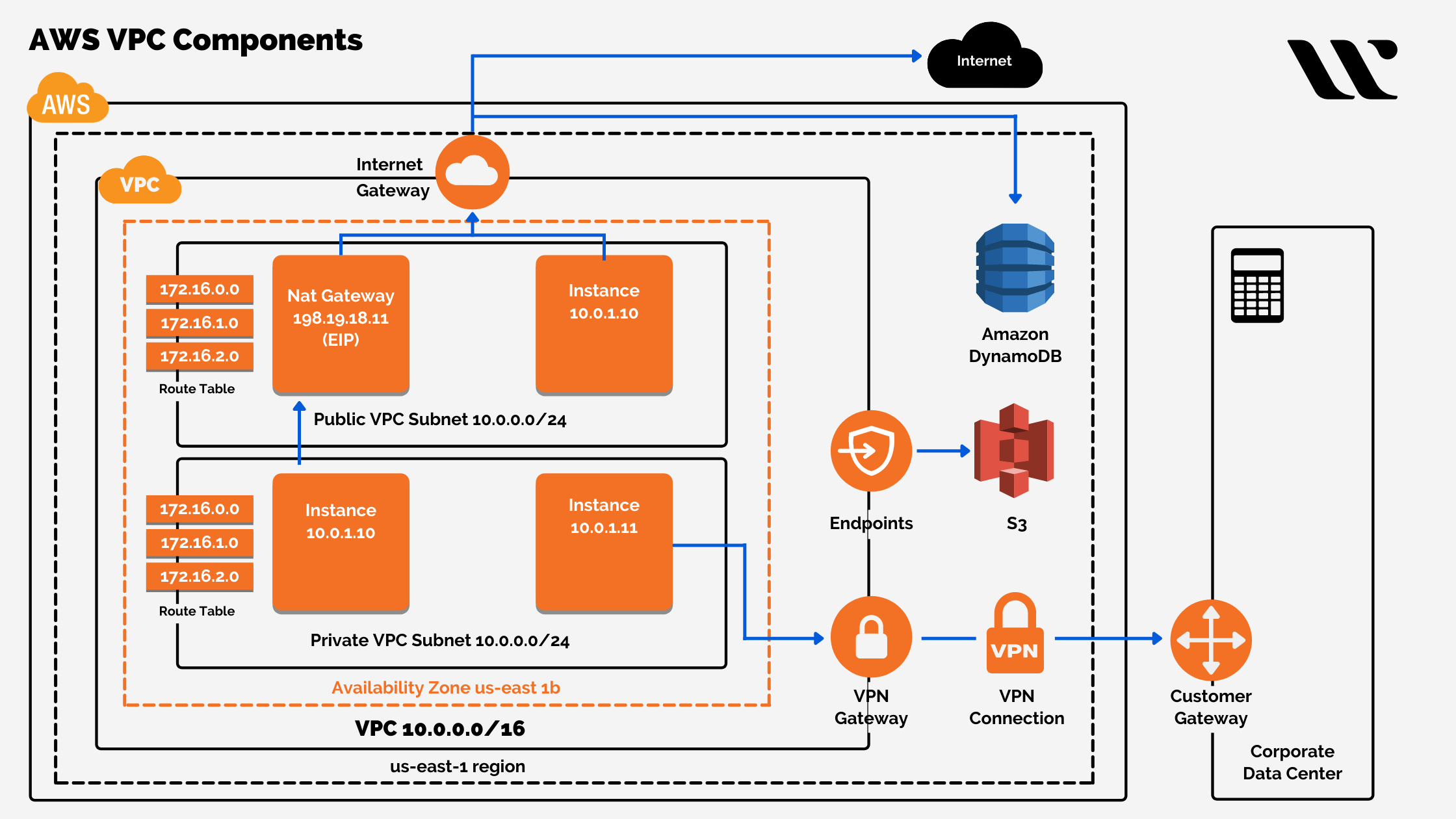
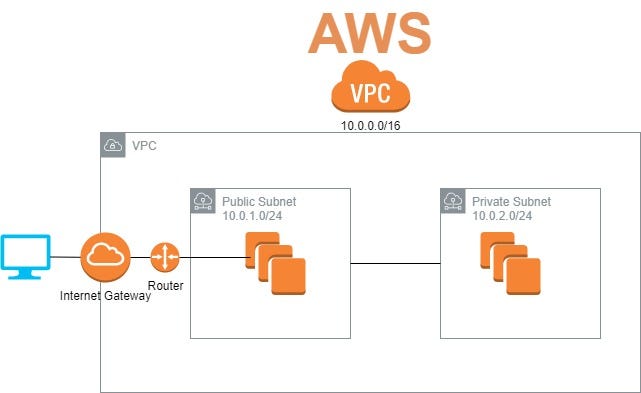
Before diving into connection methods, it's crucial to have a solid grasp of AWS VPC fundamentals and how to design a secure VPC architecture tailored for IoT. An AWS VPC is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS Cloud, giving you complete control over your virtual networking environment. This includes selecting your own IP address range, creating subnets, and configuring route tables and network gateways. For IoT, this isolation is key to preventing unauthorized access and segmenting your devices from other parts of your cloud infrastructure.
VPC Fundamentals for IoT Devices
When thinking about IoT devices within a VPC, consider the following core components:
- Subnets: You can divide your VPC into one or more subnets. For IoT, it's often beneficial to have public subnets for resources that need internet access (e.g., a load balancer) and private subnets for your backend IoT applications and databases. Your IoT devices might connect into private subnets through various secure tunneling methods.
- Security Groups: These act as virtual firewalls that control inbound and outbound traffic for instances within your VPC. For IoT, security groups are vital for restricting communication to only necessary ports and protocols, ensuring that only authorized traffic can reach your IoT applications.
- Network Access Control Lists (NACLs): These are stateless firewalls that control traffic to and from subnets. While security groups are more granular, NACLs provide an additional layer of defense at the subnet level.
- Route Tables: These determine where network traffic from your subnets is directed. Correct routing is essential for ensuring your IoT devices can reach the necessary services within your VPC and vice versa.
- Internet Gateway (IGW) / NAT Gateway (NAT GW): An IGW allows public internet access to your VPC, typically for public subnets. A NAT Gateway allows instances in private subnets to initiate outbound connections to the internet while preventing inbound connections from the internet, a common pattern for IoT devices that need to send data out but should not be directly accessible from the internet.
By carefully configuring these elements, you can build a robust and secure foundation for your IoT infrastructure within AWS.
Designing a Secure VPC Architecture
Designing a secure AWS VPC architecture for IoT involves several best practices:
- Principle of Least Privilege: Grant only the minimum necessary permissions to your IoT devices and the services they interact with.
- Network Segmentation: Use subnets and security groups to segment your network. For example, you might have a dedicated "management VPC" for administrative tasks and a "production VPC" for your core IoT operations. The management VPC uses VPNs through a customer gateway to connect to a single device in the data center, while the production VPC uses a virtual private gateway with two connections for redundancy. This separation enhances security by limiting the blast radius of any potential breach.
- Private Connectivity: Wherever possible, use private network connections instead of exposing services to the public internet. This includes using AWS PrivateLink, VPNs, or Direct Connect.
- Logging and Monitoring: Implement comprehensive logging using AWS CloudTrail and VPC Flow Logs to monitor network activity and detect anomalies. Integrate with Amazon CloudWatch for alerts.
- Regular Audits: Periodically review your VPC configurations, security groups, and NACLs to ensure they align with your security policies and evolving threats.
A well-designed VPC architecture is the cornerstone of securely connecting remote IoT devices to AWS, providing the necessary isolation and control.
Raspberry Pi: The Remote IoT Device
The Raspberry Pi is an incredibly versatile and popular choice for remote IoT deployments due to its low cost, small form factor, and powerful capabilities. It can run various operating systems, including Raspbian (now Raspberry Pi OS), and supports a wide range of programming languages and libraries. Its GPIO pins allow it to interface with sensors, actuators, and other hardware components, making it ideal for collecting data, performing edge computing, and interacting with the physical world.
When integrating a Raspberry Pi into an AWS IoT ecosystem, it typically acts as an edge device. This means it collects data locally, performs some initial processing, and then securely transmits relevant information to the AWS cloud for further analysis, storage, or action. By integrating remote IoT VPC SSH with Raspberry Pi and AWS, homeowners can remotely control lighting, temperature, and security systems from their smartphones or other devices. The challenge with Raspberry Pi, like any remote IoT device, is ensuring its connection back to your AWS VPC is secure, resilient, and manageable, especially when operating in potentially untrusted environments.
The small footprint and power efficiency of the Raspberry Pi make it suitable for deployments where power sources are limited or intermittent. Its robust community support also means a wealth of resources are available for troubleshooting and development. However, its resource constraints compared to full-fledged servers mean that security configurations must be efficient and carefully managed to avoid performance degradation. This guide will walk you through the process of securely connecting remote IoT devices using Raspberry Pi on AWS VPC, ensuring robust protection for your network.
Core Technologies for Secure IoT-VPC Connection
To securely connect remote IoT devices to an AWS VPC, several key AWS networking and security technologies come into play. These technologies provide the encrypted, private pathways necessary to protect your data in transit.
VPN Connections: Customer Gateway and Virtual Private Gateway
A common and flexible method for securely connecting remote IoT devices to an AWS VPC is through a Virtual Private Network (VPN) connection. AWS offers two primary components for site-to-site VPNs:
- Virtual Private Gateway (VPG): This is the VPN concentrator on the Amazon side of the VPN connection. You attach a VPG to your VPC, and it acts as the endpoint for your VPN tunnel.
- Customer Gateway (CGW): This is a resource in AWS that provides information to AWS about your customer gateway device (e.g., your Raspberry Pi acting as a VPN client or a dedicated VPN appliance). It includes the public IP address of your device and routing information.
To establish a VPN connection, you configure your Raspberry Pi with a VPN client (e.g., OpenVPN, strongSwan for IPsec) that connects to the Virtual Private Gateway in your AWS VPC. This creates an encrypted tunnel over the public internet, making your IoT data secure. The production VPC uses a virtual private gateway with two connections for redundancy, ensuring high availability for your IoT data flow.
AWS Direct Connect Gateway for Enterprise Scale
For organizations with a large number of IoT devices, high bandwidth requirements, or strict latency needs, AWS Direct Connect offers a dedicated network connection from your on-premises environment to AWS. This bypasses the public internet entirely, providing a more consistent and secure network experience. To connect multiple VPCs across different AWS regions or accounts to a single Direct Connect connection, you use an AWS Direct Connect Gateway.
You associate an AWS Direct Connect Gateway with any of the following: a virtual private gateway, a Direct Connect connection, or a transit gateway. This allows you to extend your on-premises network to multiple VPCs globally over a private, high-bandwidth connection. While Direct Connect is typically used for data centers, a scenario could involve a local IoT aggregation point (e.g., a small edge data center) connected via Direct Connect, which then funnels data from many remote IoT devices into your AWS VPCs. This provides an extremely secure and high-performance backbone for your IoT data.
AWS PrivateLink for Private VPC Connectivity
AWS PrivateLink allows you to privately connect your VPC to supported AWS services, services hosted by other AWS accounts (VPC endpoint services), and supported AWS Marketplace partner services, without requiring an internet gateway, NAT device, VPN connection, or Direct Connect. This is a powerful option for enhancing security by keeping all traffic within the AWS network.
For IoT, PrivateLink is particularly useful when your IoT devices need to interact with specific AWS services (e.g., AWS IoT Core, Amazon S3, Amazon Kinesis) or applications hosted in other VPCs. Instead of routing traffic over the public internet or through a VPN, you create a VPC endpoint for the service. This endpoint provides a private IP address within your VPC, allowing your IoT devices to communicate with the service as if it were hosted directly within your VPC. This significantly reduces the attack surface and simplifies network architecture for secure communication.
Step-by-Step: Securely Connecting Remote IoT to AWS VPC
This section outlines the general steps to securely connect remote IoT devices, specifically a Raspberry Pi, to your AWS VPC. Securely connecting remote IoT devices involves multiple layers of networking, security protocols, and configuration settings.
Configuring Your Raspberry Pi for Secure Connection
The first step is to configure the Raspberry Pi with the necessary software. This typically involves:
- Operating System Setup: Install the latest Raspberry Pi OS (formerly Raspbian) on your Raspberry Pi. Ensure it's fully updated.
- VPN Client Installation: If you're using a VPN connection, install a suitable VPN client. OpenVPN is a popular choice due to its open-source nature and robust security features. You'll need to configure the client with the VPN credentials and configuration files obtained from your AWS Virtual Private Gateway.
- AWS IoT SDK Installation (Optional but Recommended): For direct integration with AWS IoT Core, install the AWS IoT Device SDK for Python (or your preferred language). This SDK simplifies device authentication, message publishing, and subscribing to topics using MQTT, a lightweight messaging protocol ideal for IoT. The SDK handles secure communication (TLS/SSL) and authentication using X.509 certificates.
- Security Hardening:
- Change default passwords.
- Disable unnecessary services.
- Enable a firewall (e.g., `ufw`) on the Raspberry Pi to restrict inbound connections.
- Keep the OS and all software up-to-date.
- Use SSH keys for remote access instead of passwords.
Once configured, the Raspberry Pi will be ready to establish a secure, encrypted tunnel or connection to your AWS VPC.
Setting Up Your AWS VPC for IoT Integration
The second crucial step is to configure the AWS VPC, creating the necessary security and networking components:
- VPC Creation: If you don't already have one, create a new VPC with a suitable CIDR block.
- Subnet Creation: Create private subnets where your IoT applications and backend services will reside. If using a VPN, your Virtual Private Gateway will route traffic into these private subnets.
- Security Group Configuration: Create security groups for your IoT applications and services within the VPC. These security groups should only allow inbound traffic from your VPN connection (or PrivateLink endpoint) on the necessary ports (e.g., MQTT port 8883 for AWS IoT Core, SSH port 22 for management if strictly controlled).
- Virtual Private Gateway (VPG) Setup: Create a Virtual Private Gateway and attach it to your VPC.
- Customer Gateway (CGW) Setup: Create a Customer Gateway that references the public IP address of your Raspberry Pi (or the VPN endpoint it connects through).
- Site-to-Site VPN Connection: Create a Site-to-Site VPN connection between your VPG and CGW. AWS will provide configuration files for your VPN client (e.g., OpenVPN configuration).
- Route Table Configuration: Update your VPC's route tables to ensure that traffic destined for your Raspberry Pi's local network is routed through the Virtual Private Gateway. Conversely, ensure your Raspberry Pi's local network routes traffic destined for your VPC through the VPN tunnel.
- AWS IoT Core Setup (if using SDK):
- Create an AWS IoT thing for your Raspberry Pi.
- Generate and attach X.509 certificates and a policy to the thing. The policy should grant permissions for publishing and subscribing to specific MQTT topics.
- Configure your Raspberry Pi with these certificates and the AWS IoT endpoint.
- AWS PrivateLink (Optional): If you plan to use PrivateLink, create VPC endpoints for the AWS services your IoT devices need to access privately (e.g., S3, Kinesis, IoT Core).
By following these steps, you establish a secure, encrypted channel from your remote Raspberry Pi directly into your isolated AWS VPC, ensuring robust protection for your network and data.
Best Practices for Robust IoT Security in AWS
Beyond the core connection, several best practices ensure ongoing robust security for your IoT ecosystem within AWS VPC:
- Identity and Access Management (IAM): Use IAM roles and policies to control access to AWS resources. For IoT devices, leverage AWS IoT policies to grant granular permissions to devices for publishing and subscribing to MQTT topics. Avoid hardcoding credentials.
- Certificate Management: Implement a robust certificate management strategy for your IoT devices. AWS IoT Core provides features for device certificate registration and revocation. Rotate certificates regularly.
- Data Encryption: Encrypt data both in transit (using TLS/SSL for VPNs, PrivateLink, or AWS IoT Core's secure endpoints) and at rest (using AWS Key Management Service (KMS) for data stored in S3, DynamoDB, etc.).
- Regular Software Updates: Keep the operating system, firmware, and all software on your Raspberry Pi and other IoT devices updated to patch known vulnerabilities. This is crucial for maintaining a secure connection.
- Monitoring and Logging: Utilize AWS CloudWatch, CloudTrail, and VPC Flow Logs to monitor network traffic, API calls, and device activity. Set up alerts for suspicious behavior or unauthorized access attempts. Consider integrating with AWS Security Hub for centralized security posture management.
- Device Shadow and State Management: Use AWS IoT Device Shadow service to maintain a persistent, virtual representation of your device's state. This allows applications to interact with the device even when it's offline, and helps in managing device configurations securely.
- Edge Computing Security: If performing edge computing on the Raspberry Pi, ensure that the code running on the device is secure, regularly scanned for vulnerabilities, and has proper access controls.
- Disaster Recovery and High Availability: Design your AWS VPC and IoT architecture with redundancy in mind. Use multiple Availability Zones for your VPC resources and consider redundant VPN tunnels or Direct Connect links to ensure continuous operation.
Adhering to these best practices significantly enhances the overall security posture of your remote IoT deployment on AWS, protecting your data and preventing security breaches.
Diagnosing and Troubleshooting Connection Issues
Despite careful configuration, issues can arise when securely connecting remote IoT devices to an AWS VPC. This article will walk you through the process of diagnosing and resolving issues related to securely connecting remote IoT devices to an AWS VPC. Securely connecting remote IoT devices involves multiple layers of networking, security protocols, and configuration settings. Here's a systematic approach to troubleshooting:
- Check Network Connectivity:
- Raspberry Pi Side: Verify the Raspberry Pi has internet access. Check its local network configuration (IP address, gateway, DNS).
- VPN Connection Status: On the Raspberry Pi, check the status of your VPN client. Is the tunnel established? Are there any errors in the VPN client logs?
- AWS Side: In the AWS Management Console, check the status of your Site-to-Site VPN connection. Is it "UP"? Check the health of your Virtual Private Gateway and Customer Gateway.
- Review Security Group and NACL Rules:
- Ensure that your security groups and NACLs in the AWS VPC allow the necessary inbound and outbound traffic from your Raspberry Pi's IP range (or the VPN tunnel's IP range) to your IoT applications and services.
- Verify that your Raspberry Pi's local firewall (e.g., `ufw`) isn't blocking outbound VPN traffic or inbound responses.
- Inspect Route Tables:
- AWS VPC Route Tables: Confirm that the route tables associated with your subnets correctly direct traffic destined for your Raspberry Pi's network through the Virtual Private Gateway.
- Raspberry Pi Route Table: On the Raspberry Pi, verify that its routing table correctly directs traffic destined for your AWS VPC's CIDR block through the VPN tunnel.
- Examine Logs:
- VPC Flow Logs: Enable VPC Flow Logs for your subnets to capture information about IP traffic going to and from network interfaces in your VPC. This can help identify if traffic is reaching your VPC and if it's being blocked by security groups or NACLs.
- AWS CloudTrail: Review CloudTrail logs for any API calls related to your VPC, VPN, or IoT Core configurations that might indicate recent changes or errors.
- AWS IoT Core Logs: If using AWS IoT Core, check the CloudWatch logs associated with your IoT rules and device activity for errors related to message ingestion or policy denials.
- Certificate and Policy Issues (for AWS IoT Core):
- Verify that the X.509 certificates on your Raspberry Pi are correct, unexpired, and properly associated with your AWS IoT thing.
- Ensure the AWS IoT policy attached to your thing grants the necessary permissions (e.g., `iot:Connect`, `iot:Publish`, `iot:Subscribe`) for the actions your device is trying to perform.
- MTU Mismatch: Sometimes, a Maximum Transmission Unit (MTU) mismatch between the Raspberry Pi and the VPN tunnel can cause packet fragmentation and connectivity issues. Experiment with adjusting the MTU size on the Raspberry Pi's VPN interface.
By systematically checking these layers, you can effectively diagnose and resolve most issues related to securely connecting remote IoT devices to an AWS VPC. By the end of this article, you'll have a clear understanding of these troubleshooting steps.
Real-World Applications and Use Cases
The ability to securely connect remote IoT devices to an AWS VPC opens up a myriad of real-world applications across various sectors:
- Smart Home Automation: By integrating remote IoT VPC SSH with Raspberry Pi and AWS, homeowners can remotely control lighting, temperature, and security systems from their smartphones or other devices. This secure connection ensures that sensitive home data remains private and protected from unauthorized access.
- Industrial IoT (IIoT): In manufacturing, remote Raspberry Pis can monitor machinery, collect sensor data (temperature, pressure, vibration), and send it securely to an AWS VPC for predictive maintenance analytics. This prevents costly downtime and optimizes operational efficiency.
- Agriculture Technology (AgriTech): IoT devices in remote farms can monitor soil conditions, crop health, and irrigation systems. Secure connections to AWS VPC enable real-time data analysis, automated irrigation, and early detection of issues, leading to better yields and resource management.
- Environmental Monitoring: Raspberry Pis deployed in remote locations can collect environmental data (air quality, water levels, weather patterns). Securely sending this data to AWS VPC allows for large-scale environmental analysis and early warning systems for natural disasters.
- Retail Analytics: IoT sensors in retail stores can track customer movement, inventory levels, and shelf temperatures. Securely connecting these devices to AWS VPC allows retailers to gain insights into customer behavior, optimize store layouts, and manage inventory more efficiently, all while protecting sensitive business data.
- Healthcare Monitoring: Wearable IoT devices or remote patient monitoring systems can securely transmit vital signs and health data to a healthcare provider's AWS VPC. This enables remote patient care, emergency alerts, and secure storage of sensitive medical information, adhering to strict compliance regulations.
Are you ready to build a robust and secure connection between your Raspberry Pi, located in a remote IoT environment, and your AWS server residing within a virtual private cloud? These examples highlight the transformative power of securely connected IoT, where data integrity and privacy are paramount for success. Whether you're a network administrator, DevOps engineer, or an IoT developer, mastering these connections is key to unlocking the full potential of your IoT deployments.
Conclusion
Securing the connection between your remote IoT devices and your AWS VPC is not merely a technical task; it's a strategic imperative that safeguards your data, ensures operational continuity, and builds trust in your IoT solutions. This guide has navigated the intricate landscape of securely connecting remote IoT devices to an AWS virtual private cloud (VPC), specifically focusing on leveraging Raspberry Pi as a versatile edge device. From understanding the foundational elements of AWS VPC to implementing advanced secure connectivity options like VPNs, Direct Connect, and PrivateLink, we've covered the essential components for a robust and secure IoT architecture.
By the end of this article, you will have a comprehensive understanding of securely connecting remote IoT VPC using Raspberry Pi on AWS. We’ve walked through the process of configuring your Raspberry Pi, setting up your AWS VPC, and delved into best practices for maintaining a strong security posture. We also equipped you with strategies for diagnosing and resolving common connection issues, ensuring your IoT deployment remains resilient. And there you have it—a comprehensive guide to securely connecting remote IoT devices to AWS VPC using Raspberry Pi, from setting up your VPC to integrating AWS IoT.
The journey to a truly secure IoT ecosystem is ongoing, requiring continuous vigilance, regular updates, and adherence to best practices. We encourage you to apply the knowledge gained from this guide to your own IoT projects, building secure, reliable, and innovative solutions. Have you implemented a secure IoT connection using AWS VPC and Raspberry Pi? Share your experiences, challenges, or tips in the comments below! If you found this article helpful, consider exploring other related guides on our site to further enhance your cloud and IoT security expertise.
AWS Virtual Private Cloud - Guide - Whizlabs Blog
AWS Custom VPC. I wanted to launch & connect my EC2… | by Naveen Singh
What is AWS VPC: Dissecting AWS’s Virtual Private Cloud (VPC)