Mastering Secure IoT: Choosing The Best SSH Connect IoT Device Solutions
**In today's interconnected world, the proliferation of smart devices has transformed industries and daily life. From smart homes to industrial automation, the Internet of Things (IoT) is at the forefront of innovation. However, with this unprecedented connectivity comes a critical challenge: ensuring the security and efficient management of these devices. This is where the concept of the "best SSH connect IoT device" becomes not just a convenience, but an absolute necessity for anyone involved in IoT, whether you're an enthusiast tinkering with a Raspberry Pi or a developer managing a fleet of sensors.
IoT remote monitoring involves the surveillance of smart technology as they operate in tandem with each other. Typically, an administrator uses a software program or application to view the status of each IoT device from a centralized digital control center. From here, administrators can change configurations, retrieve data, or troubleshoot issues without physical presence. However, for these remote operations to be truly effective and safe, a secure communication channel is paramount. Secure Shell (SSH) emerges as the undisputed champion in this regard, offering a powerful and reliable solution for securing remote access to IoT devices. This guide will explore the best SSH remote access tools for IoT, focusing on security, ease of use, and scalability, ensuring your IoT ecosystem remains robust and protected.
Table of Contents
- The Indispensable Role of SSH in IoT Remote Monitoring
- Understanding SSH: The Secure Shell Protocol for IoT
- Why Secure Remote Access is Paramount for IoT Devices
- Key Considerations for Choosing the Best SSH Connect IoT Device Solution
- Top SSH Clients and Tools for IoT Device Management
- Practical Steps: Connecting to Your IoT Device via SSH
- Essential Security Best Practices for IoT SSH Remote Access
- When SSH Might Not Be Enough: Advanced IoT Remote Management
The Indispensable Role of SSH in IoT Remote Monitoring
In the realm of IoT, devices are often deployed in remote or hard-to-reach locations. Imagine a network of environmental sensors in a vast agricultural field, smart meters across a city, or industrial machinery on a factory floor. Manually checking each device's status or performing updates would be impractical, if not impossible. This is precisely where IoT remote monitoring steps in, allowing administrators to oversee these devices from a centralized digital control center. From this vantage point, administrators can change parameters, push firmware updates, and diagnose issues.
However, the critical element underpinning this remote capability is security. Without a secure channel, remote access becomes a significant vulnerability, exposing sensitive data and device functionality to potential threats. This is why IoT remote SSH connection is a perfect way to securely monitor and manage IoT devices remotely. SSH, or Secure Shell, provides an encrypted tunnel for communication, ensuring that all data exchanged between the administrator's workstation and the IoT device remains confidential and protected from eavesdropping or tampering. Whether you are an IoT enthusiast or a developer working on IoT projects, understanding how to SSH into an IoT device is crucial for effective management and safeguarding your deployed solutions.
Understanding SSH: The Secure Shell Protocol for IoT
At its core, SSH is a cryptographic network protocol that enables secure data communication between two networked devices. It's designed to provide a secure channel over an unsecured network by using strong encryption algorithms. For IoT, SSH provides a way for administrators to connect remotely and interact with devices as if they were physically present, all while ensuring the integrity and confidentiality of the session.
When you establish an SSH connection, the client (your computer) and the server (your IoT device) first negotiate a secure encrypted channel. This involves exchanging cryptographic keys and agreeing on encryption algorithms. Once the secure channel is established, all subsequent communication – commands, data, and responses – is encrypted. This means that even if a malicious actor intercepts the network traffic, they would only see scrambled, unreadable data. This robust encryption is what makes SSH a powerful and reliable solution for securing remote access to IoT devices, ensuring that sensitive information, commands, and device configurations are protected in transit. SSH's role in ensuring the safety and integrity of data transmitted between devices is truly crucial, making it an indispensable tool for any IoT deployment.
Why Secure Remote Access is Paramount for IoT Devices
The sheer volume and diversity of IoT devices, from simple sensors to complex industrial controllers, present a vast attack surface if not properly secured. Insecure remote access can lead to catastrophic consequences, both for individual users and large organizations. Consider the following risks:
- Data Breaches: IoT devices often collect sensitive data, such as personal health information, location data, or proprietary industrial processes. Unauthorized access can lead to this data being stolen, misused, or sold.
- Device Hijacking: Compromised IoT devices can be repurposed by attackers for malicious activities, such as launching Distributed Denial of Service (DDoS) attacks (as seen with the Mirai botnet), spreading malware, or even acting as entry points into larger corporate networks.
- Operational Disruptions: In industrial IoT (IIoT) or critical infrastructure, a compromised device can lead to operational shutdowns, equipment damage, or even physical harm. Imagine a smart factory where production lines are halted or manipulated by an external intruder.
- Privacy Violations: Smart home devices, cameras, and voice assistants can become tools for surveillance if their remote access is not secured, leading to severe privacy breaches.
Secure Shell (SSH) provides a secure way to access and manage IoT devices remotely, ensuring both functionality and security. By utilizing SSH, you leverage its cryptographic capabilities to prevent these scenarios. SSH ensures that only authorized individuals can connect to your devices, that their identities are verified, and that all data exchanged is encrypted and tamper-proof. This not only protects your data and devices but also maintains the integrity and reliability of your entire IoT ecosystem. For those dealing with "Your Money or Your Life" (YMYL) implications, such as healthcare IoT or critical infrastructure, the robust security offered by SSH is not just a feature, but a fundamental requirement for trust and safety.
Key Considerations for Choosing the Best SSH Connect IoT Device Solution
When looking for the best SSH connect IoT device solution, it's not a one-size-fits-all scenario. The ideal choice depends on your specific needs, the scale of your deployment, and your technical expertise. Here are the crucial factors to consider:
- Security Features:
- Encryption Standards: Ensure the client and server support strong, modern encryption algorithms (e.g., AES-256, ChaCha20-Poly1305) and secure key exchange methods (e.g., ECDH, Curve25519).
- Authentication Methods: Prioritize solutions that support robust authentication, especially public-key authentication (SSH keys) over password-based authentication. This is significantly more secure.
- Two-Factor Authentication (2FA): Some advanced clients or setups can integrate with 2FA for an extra layer of security.
- Ease of Use:
- User Interface (UI): For beginners or those managing many devices, a graphical user interface (GUI) can be more intuitive than a command-line interface (CLI).
- Session Management: The ability to save connection profiles, credentials, and configurations for multiple devices can save significant time and reduce errors.
- Setup Complexity: How easy is it to install, configure, and get started with the client and enable SSH on the IoT device?
- Scalability:
- Managing Multiple Devices: If you're dealing with a large fleet of IoT devices, the solution should offer features for bulk management, scripting, or integration with automation tools.
- Network Configuration: Consider how the solution handles devices behind NATs, firewalls, or in dynamic IP environments.
- Compatibility:
- Operating System Support: Does the SSH client run on your preferred operating system (Windows, macOS, Linux, mobile)?
- IoT Platform Support: Is the solution compatible with the specific IoT devices or platforms you are using, such as Raspberry Pi, ESP32, Arduino, or industrial PLCs?
- Reliability and Performance:
- Connection Stability: The client should maintain stable connections, especially over less reliable networks.
- Resource Usage: For resource-constrained IoT devices, the SSH server component should be lightweight and efficient.
- Additional Features:
- SFTP/SCP: Secure File Transfer Protocol (SFTP) or Secure Copy Protocol (SCP) for securely transferring files to and from your IoT devices.
- Port Forwarding/Tunneling: For securely accessing other services running on the IoT device or its local network.
- Terminal Emulation: Support for various terminal types and features like scrollback, search, and custom themes.
By carefully evaluating these considerations, you can select the best SSH connect IoT device solution that aligns with your operational requirements and security posture.
Top SSH Clients and Tools for IoT Device Management
With the growing number of IoT devices, selecting the right SSH client is paramount for efficient and secure management. Below are some of the best tools for managing IoT devices and Raspberry Pi through SSH, each offering unique strengths.
PuTTY: A Classic for Windows Users
PuTTY is a lightweight and versatile SSH client for Windows users, and arguably one of the most widely recognized. It offers secure network service access across an unprotected network. Its popularity stems from its simplicity and effectiveness.
- Features: Supports SSH, Telnet, Rlogin, and raw socket connections. It allows users to save session configurations, making it easy to reconnect to frequently accessed IoT devices. It also supports SSH key-based authentication, which is crucial for enhanced security.
- Ease of Use: Connecting to an IoT device via SSH on Windows 10 is a straightforward process with PuTTY. You’ll need an SSH client like PuTTY, the IP address of your IoT device, and the login credentials. The interface is simple, though it might appear dated to some.
- Best For: Windows users who need a reliable, no-frills SSH client for individual connections to IoT devices like Raspberry Pi. It's excellent for beginners getting started with SSH.
OpenSSH: The Ubiquitous Solution
OpenSSH is a suite of secure networking utilities based on the SSH protocol. It's the most widely used SSH implementation and is typically pre-installed on most Linux distributions and macOS. It's also available for Windows 10 and newer versions.
- Features: OpenSSH provides the core SSH client (
ssh), server (sshd), secure copy (scp), and secure file transfer (sftp) functionalities. It's highly configurable and supports a vast array of cryptographic algorithms and authentication methods. - Ease of Use: For Linux and macOS users, OpenSSH is command-line driven, making it incredibly powerful for scripting and automation. While it requires familiarity with the terminal, its flexibility is unmatched for experienced users and developers.
- Best For: Linux and macOS users, developers, and system administrators who prefer command-line tools and require robust, highly configurable SSH capabilities for managing multiple IoT devices or integrating SSH into scripts.
Termius/MobaXterm: Feature-Rich Alternatives
For users seeking more advanced features beyond basic SSH connectivity, clients like Termius and MobaXterm offer comprehensive solutions.
- Termius: A cross-platform SSH client available on Windows, macOS, Linux, Android, and iOS. It offers cloud synchronization of hosts, snippets, and themes, making it ideal for managing devices across different machines. It includes SFTP, port forwarding, and a beautiful, modern UI.
- Best For: Users who need seamless SSH access across multiple devices (desktop and mobile) and desire advanced features like cloud sync, session management, and a polished user experience.
- MobaXterm: A powerful toolbox for Windows that combines an enhanced terminal with an X11 server, a tabbed SSH client, network tools, and more. It supports SSH, Telnet, Rlogin, FTP, SFTP, and other protocols. Its multi-tabbed interface and integrated file browser are highly convenient.
- Best For: Windows users who need an all-in-one network tool, including a robust SSH client, SFTP capabilities, and even remote desktop features, often used by network engineers and developers.
Specific Tools for IoT Platforms (e.g., Raspberry Pi OS's built-in SSH)
Many IoT operating systems, like Raspberry Pi OS (formerly Raspbian), come with an SSH server pre-installed or easily enabled. This built-in functionality is crucial for remote management.
- Raspberry Pi OS SSH: By default, SSH is disabled on Raspberry Pi OS for security reasons, but it can be easily enabled via the `raspi-config` tool or by placing an empty `ssh` file in the boot directory of the SD card. Once enabled, any standard SSH client (like PuTTY or OpenSSH) can connect to it.
- Best For: Anyone working with Raspberry Pi or similar single-board computers that serve as the backbone of many IoT projects. It simplifies the server-side setup, allowing users to focus on client-side connectivity.
Choosing the best SSH connect IoT device tool depends on your specific workflow and requirements. For simple, occasional connections, PuTTY or OpenSSH might suffice. For more complex, multi-device management or cross-platform needs, Termius or MobaXterm could be the better choice.
Practical Steps: Connecting to Your IoT Device via SSH
Establishing an SSH connection to your IoT device is a fundamental skill for remote management. This guide will walk you through how to access IoT devices remotely with SSH on both Windows and Mac/Linux, highlighting the general process.
Prerequisites:
- SSH Enabled on IoT Device: Ensure that the SSH server is running and enabled on your IoT device. For Raspberry Pi, this typically involves enabling it through `raspi-config` or creating an empty `ssh` file in the boot partition.
- IoT Device's IP Address: You need the IP address of your IoT device on your local network. You can usually find this by checking your router's connected devices list, using network scanning tools (like Nmap), or by connecting a monitor and keyboard to the device and running `ifconfig` (Linux) or `ipconfig` (Windows IoT Core).
- Login Credentials: You'll need the username and password (or SSH key) for a user account on the IoT device. Common default usernames for devices like Raspberry Pi are 'pi' or 'root'.
- SSH Client: As discussed, PuTTY for Windows, or OpenSSH (built-in) for Mac/Linux.
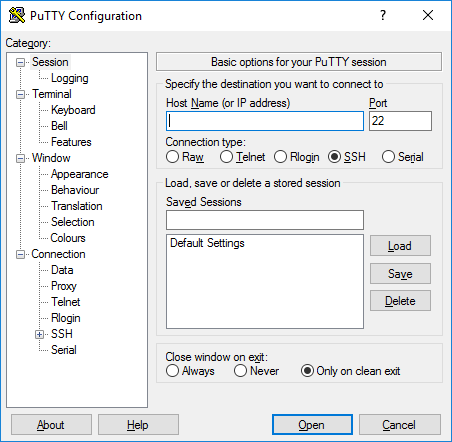
Connecting on Windows (using PuTTY):
- Download PuTTY: If you don't have it, download PuTTY from its official website.
- Launch PuTTY: Open the PuTTY application.
- Enter Connection Details:
- In the "Host Name (or IP address)" field, enter the IP address of your IoT device.
- Ensure the "Port" is set to 22 (the default SSH port).
- Select "SSH" as the connection type.
- Save Session (Optional): In the "Saved Sessions" box, give your connection a name (e.g., "My_Raspberry_Pi_IoT") and click "Save." This allows you to quickly load these settings later.
- Open Connection: Click the "Open" button.
- Security Alert (First Connection): If this is your first time connecting to the device, PuTTY will show a security alert about the server's host key not being cached. This is normal. Click "Accept" to trust the device's key.
- Login: A terminal window will open. You will be prompted for a username (e.g., `login as: pi`) and then a password. Enter your credentials.
- Success: You are now securely connected to your IoT device via SSH! You can execute commands directly on the device.
Connecting on Mac/Linux (using OpenSSH):
- Open Terminal: Launch the Terminal application (Applications > Utilities > Terminal on Mac, or search for "Terminal" on Linux).
- Use the SSH Command: The basic SSH command syntax is `ssh [username]@[IP_address]`.
- For example, if your username is 'pi' and the IP address is 192.168.1.100, you would type: `ssh pi@192.168.1.100`
- Security Prompt (First Connection): If this is your first time connecting, you'll see a message like "The authenticity of host '192.168.1.100 (192.168.1.100)' can't be established." Type `yes` and press Enter to continue. The device's host key will be added to your `known_hosts` file.
- Enter Password: You will be prompted to enter the password for the specified user. Type it (it won't show on screen) and press Enter.
- Success: You are now connected to your IoT device. You'll see the device's command prompt, ready for your input.
This straightforward process allows you to securely monitor and manage your IoT devices remotely.
Essential Security Best Practices for IoT SSH Remote Access
While SSH provides a secure foundation, its effectiveness heavily relies on how you implement and manage it. Neglecting best practices can turn a secure protocol into a potential vulnerability. These tips will help you safeguard your IoT and keep it safe from unauthorized access and cyber threats.
- Always Use Strong Passwords and Key-Based Authentication:
- Passwords: If you must use passwords, ensure they are complex (long, mix of characters, no dictionary words) and unique for each device.
- SSH Keys: This is the gold standard. Generate an SSH key pair (a public key for the IoT device, a private key for your client). This method is far more secure than passwords, as the private key never leaves your machine.
- Disable Password Authentication (if possible):
- Once you have successfully set up SSH key-based authentication, disable password authentication on your IoT device's SSH server (`sshd_config`). This prevents brute-force attacks against your passwords.
- Change the Default SSH Port:
- The default SSH port is 22. While not a security measure on its own (it's "security by obscurity"), changing it to a non-standard port (e.g., 2222 or 44321) can significantly reduce the number of automated scanning attempts and brute-force attacks against your device.
- Limit User Access:
- Create dedicated, non-root users for SSH access. Avoid using the 'root' user directly.
- Grant users only the minimum necessary permissions (principle of least privilege).
- Remove or disable default/unnecessary user accounts.
- Regularly Update Firmware and Software:
- Keep your IoT device's operating system, SSH server, and any applications up-to-date. Software updates often include
Step-by-step Guide | How to Remotely Connect to IoT Devices via SSH

How to do SSH into an IoT device? – Robocraze

Unlocking The Power Of Remote SSH IoT: A Comprehensive Guide