Fortify Your Digital Gates: SSH Key Management Best Practices
In today's interconnected digital landscape, securing remote access to systems and maintaining IT infrastructure security is paramount. Secure Shell (SSH) keys provide an essential safeguard for this, acting as digital passports that authenticate users and machines, ensuring only authorized entities can access critical resources. However, the effectiveness of these powerful cryptographic tools hinges entirely on robust SSH key management best practices. Without proper oversight, even the strongest SSH keys can become vulnerabilities, opening doors for unauthorized access, data breaches, and severe operational disruptions.
You wouldn't let hackers download permission to get root access on your organization's most sensitive systems, would you? Yet, unmanaged SSH keys can inadvertently grant precisely that level of access. This article delves into the critical importance of SSH key management, exploring how these keys work, the inherent risks and significant benefits they offer, and, most importantly, providing a comprehensive guide to the best practices you can implement today to protect your systems and network. Learn how to use SSH key management best practices to safeguard your digital infrastructure and ensure continuous regulatory compliance.
Table of Contents
- Understanding SSH Keys: The Foundation of Secure Remote Access
- Why SSH Key Management is Non-Negotiable for Your Organization's Security
- The Core Elements of Effective SSH Key Management
- 14 SSH Key Management Best Practices to Fortify Your Defenses
- Overcoming Challenges in SSH Key Management
- Regulatory Compliance and Industry Guidance (NIST)
- The Path Forward: Securing Your Digital Gates with Proactive SSH Key Management
Understanding SSH Keys: The Foundation of Secure Remote Access
SSH (Secure Shell) keys are a cryptographic method of authentication that provides a much more secure alternative to traditional password-based logins for remote access. They consist of a pair of mathematically linked keys: a public key and a private key. The public key can be freely shared and placed on any server you wish to access, while the private key must remain strictly confidential and secured on your local machine. When you attempt to connect to a server using SSH keys, the server uses your public key to encrypt a challenge. Your local machine then uses your private key to decrypt that challenge, proving your identity without ever transmitting your private key or a password over the network. This process, known as public-key cryptography, makes SSH key-based authentication incredibly robust against brute-force attacks and eavesdropping, offering a significant security upgrade over passwords alone. Although passwordless SSH is easier to manage in terms of user experience, it introduces the critical need for proper SSH key management best practices to ensure that the private keys themselves are never compromised.Why SSH Key Management is Non-Negotiable for Your Organization's Security
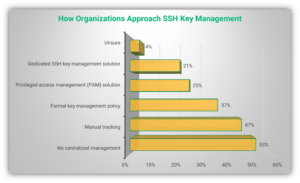
SSH key management is essential for securing remote access to systems and maintaining IT infrastructure security. It is, essentially, the practice of managing those critical admin keys so that you know at all times who has access to what, when, and why. The importance of properly managing SSH keys cannot be overstated. They are often used for privileged access, including root account passwords and other highly sensitive operations. If these keys fall into the wrong hands, the consequences can be catastrophic. Unmanaged SSH keys pose a severe security risk. They can lead to unauthorized access, data breaches, and complete system compromise. Beyond the immediate security threat, unmanaged SSH keys can lead to policy violations, failed audits, and massive regulatory penalties. Imagine the fallout if an old, forgotten SSH key belonging to a former employee is still active and used by an attacker to gain entry. This is not a hypothetical scenario; it's a common vulnerability that organizations face. A Keyfactor/Ponemon Institute report highlighted this critical gap, revealing that 63% of users surveyed consider SSH keys as the most important machine identity to manage and protect — yet all the evidence suggests that many organizations still struggle with effective management. To mitigate these risks, organizations must adopt SSH key management best practices. Properly handling SSH keys ensures that only authorized users can access your systems, protecting your sensitive data and maintaining operational integrity.The Core Elements of Effective SSH Key Management
SSH key management is the collection of strategies used to actually create, assign, and ultimately deprecate SSH keys. It involves a continuous lifecycle that spans several critical phases, each requiring meticulous attention to detail to prevent vulnerabilities. This process ensures that the keys are secure throughout their existence, from generation to eventual retirement. The two primary aspects of SSH key management involve:- Creating, distributing, and securing SSH keys: This includes generating keys with appropriate strength, securely distributing public keys to target systems, and rigorously protecting private keys.
- SSH key rotation: Regularly changing keys to minimize the window of opportunity for a compromised key to be exploited.
14 SSH Key Management Best Practices to Fortify Your Defenses
So, without further ado, let’s break down the 14 SSH key management best practices you can put to work now to protect and manage access to your organization’s IT environments. Implementing these strategies will significantly enhance your security posture and streamline your operations.1. Implement a Robust SSH Key Security Strategy
Building an SSH key security strategy is a great way to bring key generation and use under control. This strategy should define clear policies for key creation, storage, distribution, and revocation. It should outline who is authorized to generate keys, the required key strength, and the approval processes for key deployment. A well-defined strategy ensures consistency and accountability across your organization, laying the groundwork for effective SSH security and authentication.2. Automate Key Lifecycle Management
Manual SSH key management is prone to errors and becomes unmanageable at scale. Automation can help significantly lower the overhead and risk of unmanaged keys. Implement tools and scripts to automate the entire key lifecycle:- **Generation:** Automatically generate keys with required cryptographic strength.
- **Distribution:** Securely distribute public keys to authorized servers.
- **Rotation:** Automate periodic key rotation.
- **Deprecation/Revocation:** Automatically revoke or deprecate keys when they are no longer needed (e.g., employee departure, project completion).
3. Regularly Audit and Rotate SSH Keys
Regularly audit your SSH keys and rotate them, particularly those used for critical operations like signing or root access. Auditing helps identify rogue, orphaned, or expired keys that could pose a risk. Key rotation minimizes the impact of a potential compromise by limiting the lifespan of any given key. Establish a clear schedule for rotation based on the sensitivity of the systems the keys access.4. Enforce Strong Key Generation Standards
Always generate SSH keys with sufficient cryptographic strength. For RSA keys, a minimum of 2048 bits is standard, with 4096 bits being preferred for higher security. For ECDSA or Ed25519 keys, ensure they meet current cryptographic recommendations. Using strong algorithms and key lengths is a fundamental aspect of SSH security and authentication.5. Protect Private Keys with Strong Passphrases
While SSH keys offer passwordless access to servers, your private key itself should always be protected by a strong passphrase. This adds an extra layer of security, requiring a password to unlock the private key even if an attacker gains access to your local machine. Choose a long, complex, and unique passphrase that is not easily guessed.6. Utilize Hardware Security Modules (HSMs) or Smartcards/YubiKeys
For the most sensitive private keys, consider storing them in Hardware Security Modules (HSMs) or physical security tokens like YubiKeys or smartcards. Something that may make you feel better, get a smartcard or something like a YubiKey. These devices store private keys in tamper-resistant hardware, making it extremely difficult for attackers to extract them, even if the host machine is compromised. This is a significant step in enhancing your SSH key management best practices.7. Implement Principle of Least Privilege (PoLP)
Ensure that SSH keys grant only the minimum necessary permissions. Instead of giving root access by default, configure SSH to allow access to specific user accounts with limited privileges. Leverage Access Control Lists (ACLs) to enforce granular access policies, ensuring that users can only perform actions essential to their roles. This limits the blast radius if a key is compromised.8. Centralize SSH Key Management
Centralizing the management of SSH keys provides a single pane of glass for visibility and control. This allows organizations to ensure full coverage of all SSH keys, track their usage, and enforce consistent policies. Centralized solutions can also help in quickly identifying and revoking compromised keys across the entire infrastructure.9. Record SSH Sessions for Auditing and Compliance
Implementing session recording for all SSH connections is crucial for auditing, incident response, and compliance. Recording SSH sessions provides a detailed log of user activity, which can be invaluable for forensic analysis in case of a security incident or for demonstrating compliance with regulatory requirements. Use tools like Tailscale SSH to record SSH sessions effectively.10. Enforce Key Expiration and Revocation Policies
All SSH keys should have a defined expiration date. Keys should be automatically revoked or rotated upon expiration. Furthermore, establish clear procedures for immediate key revocation in scenarios such as employee termination, suspected compromise, or project completion. This proactive approach prevents stale keys from becoming security liabilities.11. Use SSH Agent Forwarding Wisely
SSH agent forwarding can be convenient, allowing you to use a single private key from your local machine to access multiple remote servers. However, it also carries risks if not managed carefully. Ensure that agent forwarding is only enabled when absolutely necessary and that the agent itself is protected. Understand the security implications before widely deploying it.12. Implement Namespaces for Key Organization
Implementing namespaces in SSH key management helps organize and categorize keys, especially in large and complex environments. This allows for better management of access policies, easier auditing, and clear separation of keys based on their purpose, environment (e.g., production, development), or user groups.13. Integrate with Identity and Access Management (IAM) Systems
Integrate your SSH key management solution with your existing Identity and Access Management (IAM) systems. This allows for centralized user authentication, authorization, and auditing, ensuring that SSH access aligns with your broader organizational access policies. It streamlines user provisioning and de-provisioning, making it easier to manage who has access to what.14. Prepare for Incident Response
In an incident response scenario, users expect to be provisioned with credentials rapidly so they can recover services that have gone offline. A well-managed SSH key system can facilitate this. Have clear procedures for emergency key generation, distribution, and revocation. This ensures that your team can quickly regain control and restore services during a crisis, minimizing downtime and impact.Overcoming Challenges in SSH Key Management
While the benefits of SSH key-based authentication are clear, the practical implementation of robust SSH key management can be challenging. The sheer volume of SSH keys in modern enterprises, coupled with the dynamic nature of cloud infrastructure and DevOps practices, makes manual oversight nearly impossible. Organizations often struggle with:- **Discovery:** Identifying all active SSH keys across diverse environments.
- **Orphaned Keys:** Keys left behind by former employees or deprecated systems.
- **Lack of Centralization:** Decentralized key storage leading to inconsistent policies.
- **Compliance Burden:** Demonstrating adherence to regulatory requirements without proper auditing.
Regulatory Compliance and Industry Guidance (NIST)
Effective management of SSH keys is essential not only to prevent cyberattacks and maintain smooth operations but also to ensure continuous regulatory compliance. Unmanaged SSH keys can lead to massive regulatory penalties and failed audits, impacting your organization's reputation and financial health. Various compliance frameworks, such as GDPR, HIPAA, PCI DSS, and SOC 2, often require stringent access controls and audit trails, for which proper SSH key management is fundamental. To provide guidance for implementation of cryptographic key management, including SSH keys, authoritative bodies like the National Institute of Standards and Technology (NIST) have published comprehensive reports. NIST has published the NISTIR 7966 report, which offers guidance for SSH user key management, detailing primary categories of vulnerabilities and best practices for mitigation. It is therefore imperative to maintain strong standards and best practices for securing the SSH keys, aligning with established industry guidance to ensure robust protection and compliance.The Path Forward: Securing Your Digital Gates with Proactive SSH Key Management
The security of your organization's remote access and critical IT infrastructure hinges on the diligent application of SSH key management best practices. From understanding how SSH keys work to implementing a comprehensive strategy that includes automation, regular auditing, and hardware security, every step contributes to a stronger defense against cyber threats. Remember, effective SSH key management is not a one-time task but an ongoing process that requires continuous vigilance and adaptation. By embracing the strategies outlined in this article, you can significantly reduce risks, enhance your security posture, and ensure compliance with regulatory requirements. Don't let unmanaged SSH keys become the weakest link in your security chain. Take action today to learn more about the benefits, risks, and challenges of managing SSH keys, and implement these best practices to protect your systems and network. What are your biggest challenges in SSH key management? Share your thoughts and experiences in the comments below, or explore our other articles on cybersecurity best practices to further strengthen your digital defenses.
SSH key management best practices and implementation tips | TechTarget
8 SSH Key Management Best Practices to Use Right Away - InfoSec Insights
14 SSH Key Management Best Practices You Need to Know - Hashed Out by